There’s a lot happening in the world of Pi. Just when we thought the Raspberry Pi Foundation were going to take a break, they announced a new PoE+ HAT (Hardware Attached on Top) for the Pi B3+ and Pi 4, and just as soon as preorders opened up I placed my order.
Now I know what you’re thinking, don’t we already have PoE HATs for the Pis that support it? Well yes, the Pi PoE HAT was released back in 2018, and while there were some problems with it, those issues got cleared up through a recall and minor redesign. Since then, we’ve all happily used those HATs to provide up to 2.5 amps at 5 volts to the Pi, with the caveat that the USB ports are limited to a combined 1.2 amps of current.
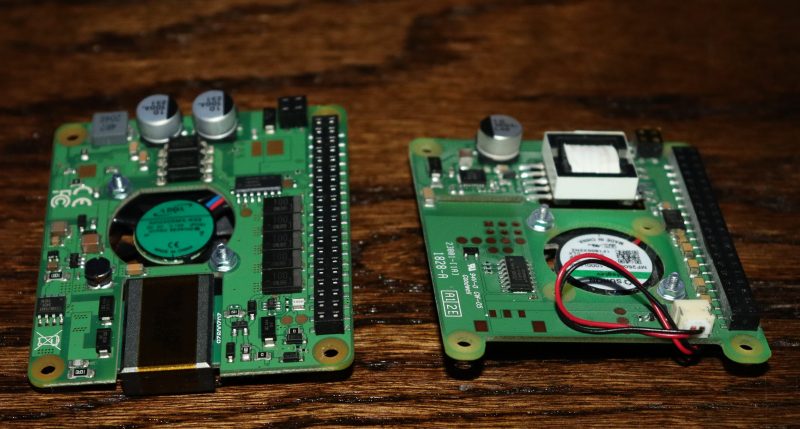
The Raspberry Pi 4 came along, and suddenly the board itself can pull over 7 watts at load. Combined with 6 watts of power for a hungry USB device or two, and we’ve exceeded the nominal 12.5 watt power budget. As a result, a handful of users that were trying to use the Pi 4 with POE were hitting power issues when powering something like dual SSD drives over USB. The obvious solution is to make the PoE HAT provide more power, but the original HAT was already at the limit of 802.3af PoE could provide, with a maximum power output of 12.95 watts.
The solution the Raspberry Pi Foundation came up with was to produce a new product, the PoE+ HAT, and sell it along side the older HAT for the same $20. The common name for 802.3at is “PoE+”, which was designed specifically for higher power devices, maxing out at 30 watts. The PoE+ HAT is officially rated to output 20 watts of power, 5 volts at 4 amps. These are the output stats, so the efficiency numbers don’t count against your power budget, and neither does the built-in fan.















