Rechargable batteries are great – they save money and hassle when using portable devices. It’s pretty common to want to recharge a battery, but less common to intentionally discharge one. Regardless, [Pawel Spychalski] is working on a device to do just that – in a controlled fashion, of course.
[Pawel] himself notes that the device isn’t something the average person would necessarily need, but it does have its applications. There are times when working with various battery chemistries that it is desired to have them held at a certain state of charge. Also, such devices can be used to measure the capacity of batteries by timing how long they take to discharge when placed under a given load.
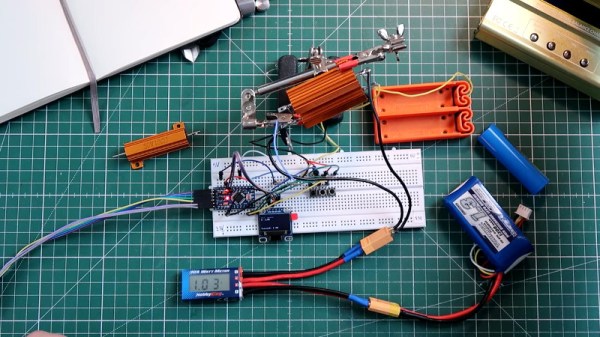
The build is one that takes advantage of the available parts of the modern hacker’s junkbox. An Arduino is used with an N-channel MOSFET to switch a resistive load. That load consists of load resistors designed for automotive use, to allow cars originally designed for filament bulbs to use LED indicator lights without the flash frequency speeding up. The resistors are 10 ohms and rated at 50 W, so they’re just about right for ganging up to discharge small LiPo batteries in a short period of time.
[Pawel] has tested the basic concept, and has things working. Next on the agenda is to find a way to get rid of the excess heat, as the current design has the resistors reaching temperatures of 158 °F (70 °C) in just a few minutes. Use some of that power to drive a fan?
Perhaps you’re working with lead acid batteries, though – in which chase, you might want to consider blasting away the sulphates?