If you’re a networking professional, there are professional tools for verifying that everything’s as it should be on the business end of an Ethernet cable. These professional tools often come along with a professional pricetag. If you’re just trying to wire up a single office, the pro gear can be overkill. Unless you make it yourself on the cheap! And now you can.
[Kristopher Marciniak] designed and built an inexpensive device that verifies the basics:
- Is the link up? Is this cable connected?
- Can it get a DHCP address?
- Can it perform a DNS lookup?
- Can it open a webpage?
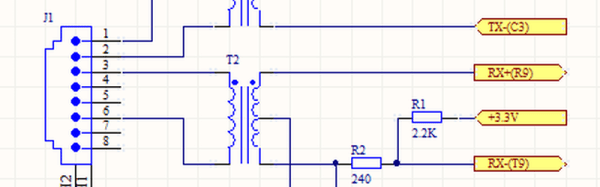
What’s going on under the hood? A Raspberry Pi, you’d think. A BeagleBoard? Our hearts were warmed to see a throwback to a more civilized age: an ENC28J60 breakout board and an Arduino Uno. That’s right, [Kristopher] replicated a couple-hundred dollar network tester for the price of a few lattes. And by using a pre-made housing, [Kristopher]’s version looks great too. Watch it work in the video just below the break.
Building an embedded network device used to be a lot more work, but it could be done. One of our favorites is still [Ian Lesnet’s] webserver on a business card from way back in 2008 which also used the ENC28J60 Ethernet chip.
Continue reading “Link Trucker Is A Tiny Networking Giant”