The disappearance of Malaysia Airlines flight MH370 after an unexplained course change sent it flying south over the Indian Ocean in March 2014 still holds the mystery of the wreck’s final location. There have been a variety of efforts to narrow down a possible search area over the years, and now we have news of a further angle from an unexpected source. It’s possible that the aircraft’s path could show up in radio scatter detectable as anomalously long-distance contacts using the amateur radio WSPR protocol.
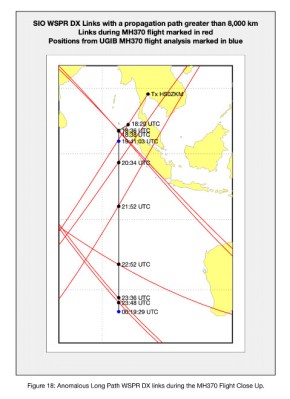 WSPR is a low-power amateur radio mode designed to probe and record the radio propagation capabilities of the atmosphere. Transmit beacons and receiving stations run continuously, and all contacts however fleeting are recorded to an online database. This can be mined by researchers with an interest in the atmosphere, but in this case it might also provide clues to the missing airliner’s flightpath. By searching for anomalously long-distance WSPR contacts whose path crosses the expected position of MH370 it’s possible to spot moments when the aircraft formed a reflector for the radio waves. These contacts can then either confirm positions already estimated using other methods, or even provide further course points. It’s an impressive demonstration of the unexpected data that can lurk in a trove such as the WSPR logbook, and also that while messing about on the airwaves the marks we leave behind us can have more benefit than simply bragging rights over the DX we’ve worked.
WSPR is a low-power amateur radio mode designed to probe and record the radio propagation capabilities of the atmosphere. Transmit beacons and receiving stations run continuously, and all contacts however fleeting are recorded to an online database. This can be mined by researchers with an interest in the atmosphere, but in this case it might also provide clues to the missing airliner’s flightpath. By searching for anomalously long-distance WSPR contacts whose path crosses the expected position of MH370 it’s possible to spot moments when the aircraft formed a reflector for the radio waves. These contacts can then either confirm positions already estimated using other methods, or even provide further course points. It’s an impressive demonstration of the unexpected data that can lurk in a trove such as the WSPR logbook, and also that while messing about on the airwaves the marks we leave behind us can have more benefit than simply bragging rights over the DX we’ve worked.
If this WSPR business intrigues you, then have a read of the piece in our $50 Ham series about it.
Header: Laurent ERRERA from L’Union, France, CC BY-SA 2.0.
[via Southgate ARC]
















