A new wind turbine installed in the Taiwan Strait went online last week, as part of the Fujian offshore wind farm project by the China Three Gorges Corporation (CTG). The system is the MySE 16-260, designed by the Ming Yang Wind Power Group, one of the leading manufacturers of wind turbines in the world. The numbers are staggering, the 16MW generator is projected to provide 66 GWh (gigawatt-hours) to the power grid annually. And this is a hefty installation, with a 260 m rotor diameter ( three each 123 m blades ) sitting atop a 152 m tower. The location is both a blessing and a curse, being an area of the Pacific that experiences Beaufort level 7 winds ( near gale, whole trees in motion ) for more than 200 days per year. Understandably, the tower and support structures are beefy, designed to survive sustained winds of 287 km/h.
This 16 MW installation surpasses the previous record holder, announced this January — the Vestas V236-15.0MW turbine with 115.5 m blades, located in Denmark’s Østerild Wind Turbine Test Center. But wait … Ming Yang also announced in January their new 18 MW turbine with 140 m long blades.
We imagine that there will eventually be a natural plateau, where the cost of the next humongous installation approaches or exceeds that of multiple smaller ones. Or will these multi-megawatt turbine systems just keep leapfrogging each other, year after year? Let us know your thoughts in the comments below.



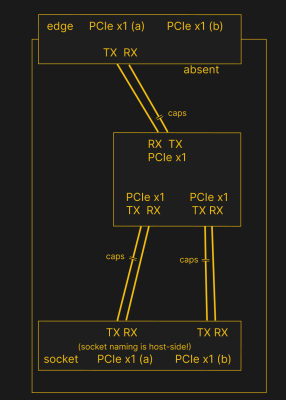 PCIe needs TX pairs connected to RX on another end, like UART – and this is non-negotiable. Connectors will use host-side naming, and vice-versa. As the diagram demonstrates, we connect the socket’s TX to chip’s RX and vice-versa; if we ever get confused, the laptop schematic is there to help us make things clear. To sum up, we only need to flip the names on the link coming to the PCIe switch, since the PCIe switch acts as a device on the card; the two links from the switch go to the E-key socket, and for that socket’s purposes, the PCIe switch acts as a host.
PCIe needs TX pairs connected to RX on another end, like UART – and this is non-negotiable. Connectors will use host-side naming, and vice-versa. As the diagram demonstrates, we connect the socket’s TX to chip’s RX and vice-versa; if we ever get confused, the laptop schematic is there to help us make things clear. To sum up, we only need to flip the names on the link coming to the PCIe switch, since the PCIe switch acts as a device on the card; the two links from the switch go to the E-key socket, and for that socket’s purposes, the PCIe switch acts as a host.













