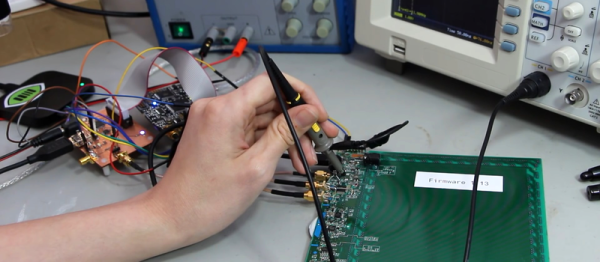
Recently ZDNet and Gizmodo published articles outlining a critical flaw in a large array of personal printers. While the number of printers with this flaw is staggering, the ramifications are even more impressive. Ultimately, any of these printers could have documents sent to them stolen even if the document was only intended to be printed as a hard copy.
Luckily the people responsible for this discovery are white-hat in nature, and the release of this information has been made public so the responsible parties can fix the security flaws. Whether or not the “responsible party” is the manufacturer of the printer, though, is still somewhat unclear because part of the exploit takes advantage of a standard that is part of almost all consumer-grade printers. The standard itself may need to be patched.
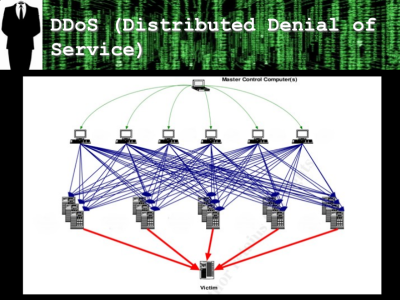
Right now, however, it doesn’t seem clear exactly how deep the rabbit hole goes. We all remember the DDoS attack that was caused by Internet of Things devices that were poorly secured, and it seems feasible that networked printers could take some part in a similar botnet if a dedicated user really needed them. At the very least, however, your printed documents might not be secure at all, and you may be seeing a patch for your printer’s firmware in the near future.