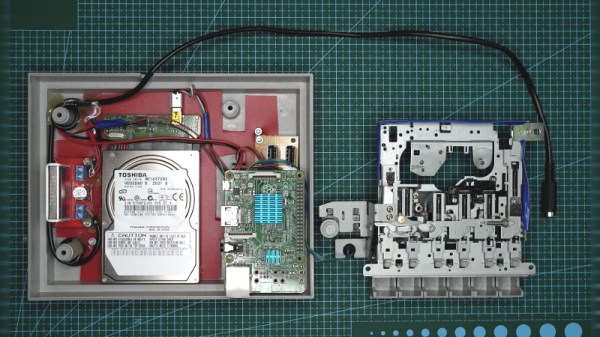
We know that a lot of our beloved readers don’t take kindly to abuse of vintage hardware, so the Atari fans in the audience may want to avert their eyes for this one. Especially if they’re particularly keen on spinning up their Jawbreaker cassette on authentic hardware, as [iot4c] has gutted an Atari XC12 Program Recorder to turn it into an enclosure for a Raspberry Pi video storage device.
Step one of this conversion was, as you might expect, removing all the original hardware from the cassette recorder case. From there, [iot4c] fitted the Raspberry Pi, a USB hard drive, and a YDS-5A DC-DC converter to power them. Depending on what the drive setup looks like, it might also make sense to add a USB powered hub. A length of Ethernet cable was left hanging out the back of the Atari XC12 so it could be plugged into the network, but a panel mount RJ45 connector could spruce things up a bit.
Of course, gutting an old piece of hardware and sticking a Pi into it isn’t exactly breaking any new ground at this point. But we did appreciate that [iot4c] went the extra mile to wire it up so the “Save” LED now doubles as a network activity indicator. Which pretty much brings it full circle in terms of functionality for a network-attached video recorder.
Earlier in the year [iot4c] converted a 65XE into a USB keyboard with the help of an Arduino Leonardo, but the vintage Atari aficionados will be happy to note that at least in that case the donor machine remained fully functional.