
We live in a connected world where social media is ubiquitous and many people feel compelled to share every waking moment with anyone who will listen. In this type of world, wearable computers like Google Glass allow us to share experiences like never before. A Glass user can take photos, record video and audio, or potentially even stream video live on the Internet with the greatest of ease. That might be great for the Glass user, but what about the rest of us? As wearable computing becomes more and more mainstream, people are naturally going to become divided on the issue of privacy. Is it a good thing to have “cyborgs” with wearable computers and cameras constantly at the ready, or is it a privacy nightmare? The cyborg war is coming, and [Julian] has already chosen his side.
It would seem that [Julian] lands on the side of the privacy advocates, based on his “glasshole” script. Glasshole is a relatively simple bash script that relies on some other common network security tools to take care of the heavy lifting. The basic premise relies on the fact that every manufacturer of network interface devices is assigned their own MAC prefix. This is a piece of the MAC address that is unique to that manufacturer.
[Julian’s] script uses a utility called arp-scan to obtain a list of all MAC addresses on a given wireless network. It then loops through each address and compares it to the known Google Glass MAC prefix. If it finds a match, it will make an audible beeping noise to alert the script user. The script then launches aireplay-ng in de-authentication mode. This will send spoofed disassociate packets to the client (in this case the Google Glass device), hopefully forcing them to disconnect from the access point. The script runs continuously, ensuring that once the device reconnects to the network it will get booted off once again. The script is designed to be run on a small Linux computer such as a Raspberry Pi or a BeagleBone black. This way, the user can carry it around with them as a sort of portable defense mechanism.
How do you fit into the cyborg war? Will you stand proudly with your computer on your face for all to see? If so, what kind of countermeasures would you deploy to prevent this type of attack from working on you? If not, what other types of interesting attacks can you think of to keep the cyborgs at bay?
[Thanks Syed]


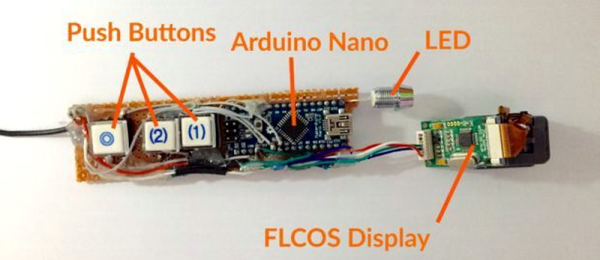
 For [Tony]’s entry for The Hackaday Prize,
For [Tony]’s entry for The Hackaday Prize, 












