It’s a simple fact that most programs created for the personal computer involve the same methods of interaction, almost regardless of purpose. Word processors, graphics utilities, even games – the vast majority of interaction is performed through a keyboard and mouse. However, sometimes it can be fun to experiment with alternative technologies for users to interact with code – Paper Programs is an exciting way to do just that.
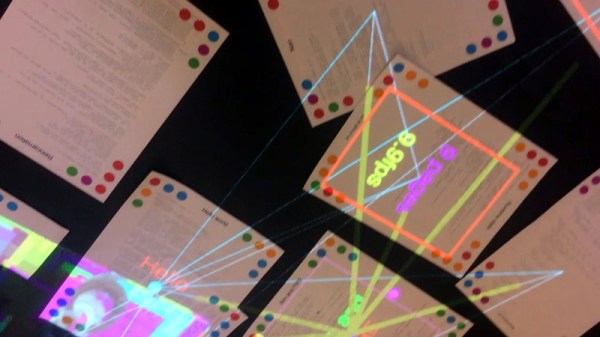
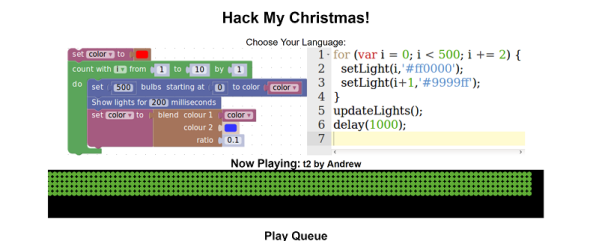
Paper Programs is a combination of a variety of existing technologies to create a way of interacting with code which is highly tangible. The setup consists of a projector, and a webcam which can see the projected area, combined with Javascript programs running in a browser. Programs can be edited in the browser, then printed out with special coloured dots around the page. When the page is placed in the projection area, these dots identify the unique program and are picked up by the webcam, and the server executes the relevant code, projecting back onto the page.
It’s a system that creates a very tactile way of interacting with a program – by moving the page around or placing different pages next to each other, programs can interact in various ways. The system is setup for collaboration as well, allowing users to edit code directly in the browser.
The project reminds us of earlier works on DIY multitouch screens, but with a greater focus on direct engagement with the underlying code. What other unique ways exist to interact with code? Let us know in the comments.