The proliferation of software-defined radio (SDR) technology has been a godsend for RF hobbyists. SDR-based receivers and transmitters have gotten so cheap that you’ve probably got a stick or two lying around your bench right now — we can see three from where we sit, in fact.
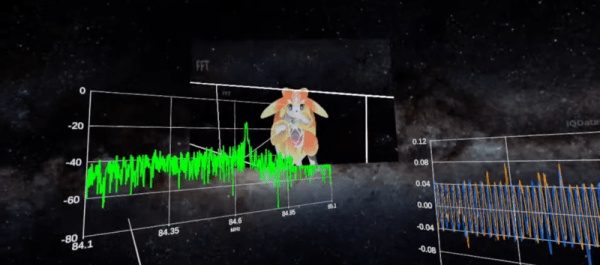
But cheap comes at a price, usually in the form of frequency stability, which can be prohibitive in some applications — especially amateur radio, where spectrum hygiene is of the utmost concern. So we were pleased to see [Tech Minds] tackle the SDR frequency stability problem by using a GPS-disciplined oscillator. The setup uses an ADALM-PLUTO SDR transceiver and a precision oscillator from Leo Bodnar Electronics. The oscillator can be programmed to output a rock-solid, GPS-disciplined signal over a wide range of frequencies. The Pluto has an external oscillator input that looks for 40 MHz, which is well within the range of the GPSDO.
Setup is as easy as plugging the oscillator’s output into the SDR’s external clock input using an SMA to UFL jumper, and tweaking the settings in the SDR and oscillator. Not all SDRs will have an external clock input, of course, so your mileage may vary. But if your gear is suitably equipped, this looks like a great way to get bang-on frequency — the video below shows just how much the undisciplined SDR can drift.
Like any good ham, [Tech Minds] is doing his bit to keep his signals clean and on target. His chief use case for this setup will be to work QO-100, amateur radio’s first geosynchronous satellite repeater. We’ve got to say that we hams living on the two-thirds of the globe not covered by this satellite are just dying to get a geosynchronous bird (or two) of our own to play with like this.
Continue reading “Bringing Some Discipline To An SDR Transmitter”