We feature plenty of printed projects here on Hackaday, though they tend to be of the three dimensional type thanks to the proliferation of affordable 3D printers. But in this case, [Milosch Meriac] has managed to put together a printable design that’s not only a very cool hack, but is made up of a scant two dimensions. His creation, which could perhaps be considered something of an interactive circuit diagram, allows anyone with a paper printer and a few passive components to make a functional low-frequency RFID sniffer.
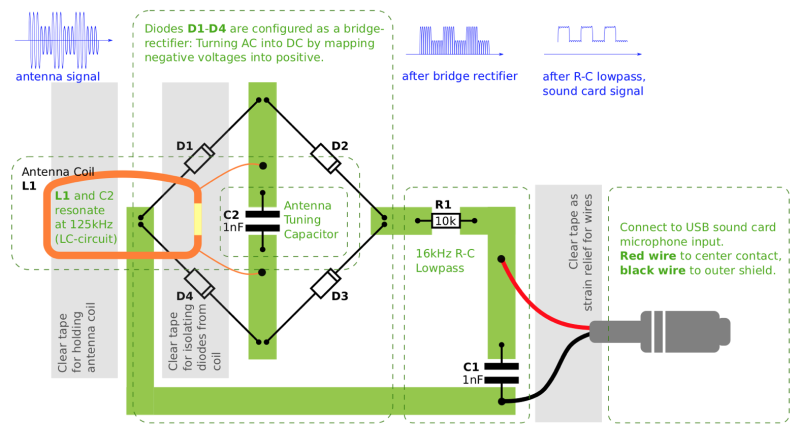 [Milosch] tells us the goal of the project is to lower the barrier for experimenting with the RFID technology that’s increasingly part of our everyday lives. Rather than having to use something expensive and complicated such as an oscilloscope, experimenters can simply plug their DIY RFID sniffer into their computer’s line-in jack and explore the produced waveform with open source tools.
[Milosch] tells us the goal of the project is to lower the barrier for experimenting with the RFID technology that’s increasingly part of our everyday lives. Rather than having to use something expensive and complicated such as an oscilloscope, experimenters can simply plug their DIY RFID sniffer into their computer’s line-in jack and explore the produced waveform with open source tools.
To create a paper RFID sniffer, you start by printing the image out on a thick piece of paper, like card stock. You then apply foil tape where indicated to serve as traces in this makeshift PCB, and start soldering on the components as described in the text. [Milosch] says the assembly procedure is so simple even a kid can do it, and the total cost of each assembled sniffer is literally pennies; making this an excellent project for schools or really any large group.
If you want to play it safe the sniffer can be connected to a USB sound card rather than your machine’s primary sound hardware, and still come in dirt cheap. [Milosch] stops short of explaining the software side of things in this particular project, but any tool which can use input from the sound card as a makeshift oscilloscope should be a good start.
In the past we’ve seen [Milosch] perform low frequency RFID sniffing through the sound card with the powerful baudline tool, but if you want a little more capable hardware, we can point you in the right direction.