The fine researchers at Google have released the juicy details on EntrySign, the AMD Zen microcode issue we first covered about a month ago. And to give away the punchline: cryptography is hard. It’s hard in lots of ways, but the AMD problem here is all about keeping track of the guarantees provided by cryptographic primitives.
Continue reading “This Week In Security: Zen Jailbreak, Telegram Exploit, And VMware Hyperjack”
telegram16 Articles
Moving The Snail Mail To WiFi
[Zak] loves getting a notification on his phone when he gets physical mail. Enough to wire his mailbox slot with an ESP8285 to send him alerts. Previously, [Zak] used a cellular-based solution as the mailbox slot was not within WiFi range. However, the network provider for the A9G GPRS module decided to move to different towers, and suddenly the module didn’t work. Unable to find a provider that had sensible pricing, he got to work redesigning the module.
The mailbox was now in a WiFi network range, meaning he no longer had to use cellular. This dramatically simplifies the design and uses an ESP-M2 module (think ESP8266 but with embedded flash). To maximize battery life, the ESP is entirely off most of the time. A reed switch triggers a 74LVC1G98 NAND gate with an inverted input. This enables the 3.3 voltage regulator. A 4uF capacitor holds the voltage regulator on for 716ms, giving the ESP8266 time to boot and drive the second pin of the logic gate so it can stay on. Once the web request completes (a call to a PHP server that takes 4-5 seconds, including WiFi association), it pulls the pin low, and the system powers off. With a custom server, [Zak] can include a few goodies, such as temperature and humidity from the SHT32-DIS sensor.
So far, the system has been chugging along for seven months and over 110 mail notifications and has only dropped 0.3v, suggesting that the battery should hold out for another year or two before recharging. The code and schematics are up on GitHub. We love the low-power focus and the handy circuit explanation that makes it easy to use in other projects.
Fixing (And Improving!) An Annoying Apartment Entry System
[Zak]’s two-floor apartment has a typical door entry control system, but the setup is less than ideally convenient. The wall-mounted telephone-like intercom is downstairs, but [Zak] is usually upstairs. What’s an enterprising hacker to do? Obviously the most elegant solution is to simply do without visitors in the first place, but [Zak] opted for a more full-featured solution to the problem.
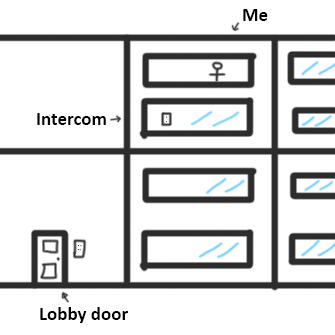
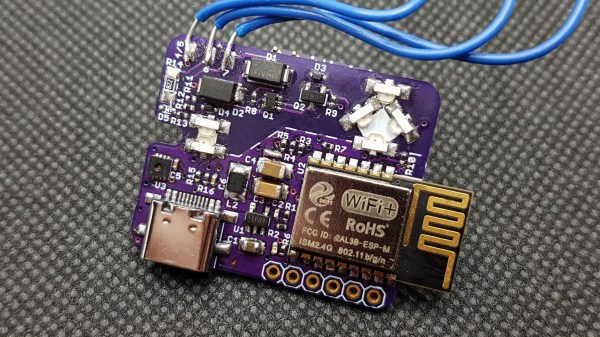
He fixed things with a custom ESP8285-based board that, with the help of opto-isolation, allows him to detect visitors and grant entry without having to be physically present at the wall-mounted intercom. It’s even integrated into Telegram, and has a few neat new features. Let’s take a look.
The first interesting bit is how [Zak] rolled his own opto-isolation. The door entry system uses 14 VAC and is frankly — electromagnetically-speaking — a very noisy device. Attaching GPIO pins directly to this system from the ESP board for interfacing is not an option. The solution in situations like this is to use opto-isolation, so that interfaced devices can be electrically isolated from one another.
Rather than use off-the-shelf options, [Zak] opted to keep things small and economical by rolling his own solution using side-mounted IR LEDs on the small interface PCB. LEDs can also act as photodiodes, so by pointing two LEDs directly at one another and driving one LED from the door control system and measuring the small amount of resulting current on the other LED, [Zak] can detect states without having to directly connect a GPIO pin.
Continue reading “Fixing (And Improving!) An Annoying Apartment Entry System”
Sending Pics To Grandma, No Smartphone Needed
When it comes to keeping in touch with the grandparents, a lack of familiarity with modern technology can get in the way. [palmerabollo] wanted to share photos with his grandmother, but found that it was difficult as she didn’t have a smartphone or an Internet connection to receive photos. Thus, a custom build for grandma was in order! (translated)
To minimise maintenance requirements, the build relies on a thermal receipt printer. Each roll of thermal paper is good for printing off about 150 images before needing a change, so it’s a low-cost, fuss-free solution with no need for ink changeovers.
A Raspberry Pi Zero 2W runs the show, paired with a HAT that provides cellular internet connectivity. Photos are sent over Telegram with some custom Python code that [palmerabollo] put together. The system uses the Python “thermalprinter” library, with the Floyd-Steinberg dithering algorithm baked in allowing nice quality even on the simple thermal printer.
It’s a fun build, and lets [palmerabollo] send his grandmother fun photos and messages without requiring any effort on her part. It’s super cute to see the photos stuck up on the refrigerator, too.
There’s plenty of fun to be had with thermal printers, so don’t be afraid to get stuck in yourself! Video after the break. Continue reading “Sending Pics To Grandma, No Smartphone Needed”
This Week In Security: ISNs, Patch Tuesday, And Clubhouse
Let’s talk TCP. Specifically, how do the different TCP connections stay distinct, and how is a third party kept from interrupting a connection? One of the mechanisms that help accomplish this feat is the TCP sequence number. Each of the two endpoints of a TCP connection tracks an incrementing 32-bit number, corresponding to the bytes sent in the connection. It’s handy, because each side can use that value to track what parts of the data stream they have received. On missing packets, a message can be sent requesting bytes 7-15 to be resent, for instance.
Each side of the connection sets their own Initial Sequence Number (ISN), and it’s important that this number is unique, as collisions can cause stream confusion. That statement should make your security spidey sense tingle. If a collision can cause problems when it happens by chance, what can a hacker do with it intentionally? Potentially quite a bit. Knowing the current sequence number, as well as a couple other pieces of information, a third party can close a TCP stream or even inject data. The attack has been around for years, originally known as the Mitnick Attack. It was originally possible because TCP implementations used a simple counter to set the ISN. Once the security ramifications of this approach were understood, the major implementations moved to a random number generation for their ISNs.
Now to this week’s story: researchers at Forescout took the time to check 11 TCP/IP stacks for vulnerability to the old Mitnick Attack (PDF Whitepaper). Of the eleven embedded stacks texted, nine have serious weaknesses in their ISN generation. Most of the vulnerable implementations use a system time value as their ISN, while several use a predictable pseudorandom algorithm that can be easily reversed.
CVEs have been assigned, and vendors notified of “NUMBER:JACK”, Forescout’s name for the research. Most of the vulnerable software already has patches available. The problem with embedded systems is that they often never get security updates. The vulnerable network stacks are in devices like IP cameras, printers, and other “invisible” software. Time will tell if this attack shows up as part of a future IoT botnet.
Continue reading “This Week In Security: ISNs, Patch Tuesday, And Clubhouse”
This Week In Security: Ubiquiti, Nissan, Zyxel, And Dovecot
You may have been one of the many of us who received an email from Ubiquiti this week, recommending a password change. The email stated that there was an unauthorized access of Ubiquiti systems, and while there wasn’t evidence of user data being accessed, there was also not enough evidence to say emphatically that user data was not accessed. Ubiquiti has mentioned that the database that may have been accessed contains a user’s name, email address, hashed password, and optionally the mailing address and phone number.
Depending on how the Ubiquiti authentication system is designed, that hashed password may be enough to log in to someone’s account. In any case, updating your password would invalidate the potentially compromised hash. This event underscores a complaint voiced by Ubiquiti users: Ubiquiti has been making it difficult to administrate hardware without a cloud-enabled account. Continue reading “This Week In Security: Ubiquiti, Nissan, Zyxel, And Dovecot”
Did Grandma Remember Her Pills? This Dispenser Tells You!
Everything has to be smart these days, and while smartening things up is a good incentive to tip your own toes into the whole IoT field, many of these undertakings are oftentimes just solutions looking for a problem. Best case, however, you actually make someone’s life easier with it, or help a person in need. For [Guli Morad] and [Dekel Binyamin], it was a bit of both when they built their automated pill dispenser: help people dependent on taking medication, and ease the mind of those worrying whether they actually remembered to.
Using an ESP8266 and a rather simple construct comprised of a set of servos with plastic sheets attached, and a plastic tube with strategically placed cuts for each pill type, a predefined amount of each of the pills can be automatically dispensed into a box — either at a given time, or on demand — using a Node-RED web interface. A reed switch mounted on the box then monitors if it was actually opened within a set time, and if not, informs emergency contacts about it through the Telegram app. Sure, a tenacious medication recipient might easily fool the system, but not even adding a precision scale to make sure the pills are actually taken out could counter a pill-reluctant patient of such kind, so it’s safe to assume that this is primarily about preventing simple forgetfulness.
Their proof of concept is currently limited to only two different types of pills, but with enough PWM outputs to control the servos, this should be easily scalable to any amount. And while the built may not be as sophisticated as some pill dispensers we’ve seen entering the Hackaday Prize a few years back, it still gets its main task done. Plus, when it comes to people’s health, a good-enough solution is always better than a perfect idea that remains unimplemented.
Continue reading “Did Grandma Remember Her Pills? This Dispenser Tells You!”