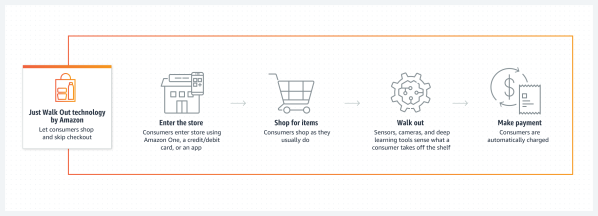
After a few years of Amazon promoting a grocery shopping experience without checkout lines and frustrating self-checkout experiences, it is now ditching its Just Walk Out technology. Conceptualized as a store where you can walk in, grab the items you need and walk out with said items automatically charged to your registered payment method, it never really caught much traction. More recently it was revealed that the technology wasn’t even as automated as portrayed, with human workers handling much of the tedium behind the scenes. This despite claims made by Amazon that it was all powered by deep machine learning and generative AI.

Instead of plastering the ceilings of stores full with cameras, it seems that Amazon instead wishes to focus on smart shopping carts that can keep track of what has been put inside them. These so-called Dash Carts are equipped with cameras and other sensors to scan barcodes on items, as well as weigh unlabeled items (like fruit), making them into somewhat of a merging of scales at the vegetable and fruit section of stores today, and the scanning tools offered at some grocery stores to help with self-checkout.
As the main problem with the Just Walk Out technology was that it required constant (700 out of 1,000 sales in 2022) human interaction, it will be interesting to see whether the return to a more traditional self-service and self-checkout model (albeit with special Dash Lanes) may speed things along. Even so, as Gizmodo notes, Amazon will still keep the Just Walk Out technology running across locations in the UK and elsewhere. Either this means the tech isn’t fully dead yet, or we will see a revival at some point in time.