We always enjoy [Kerry Wong]’s insightful teardowns, and recently, he opened up a UTG1042X arbitrary waveform generator. Getting inside was a bit of a challenge since there were no visible screws. Turns out, they were under some stickers. We always dislike that because it is very difficult to get the unit to go back together.
Once open, the case reveals it is almost completely empty. The back panel has a power supply, and the front panel has all the working circuitry. The box seems to be for holding the foot and preventing the device from getting lost on your bench.
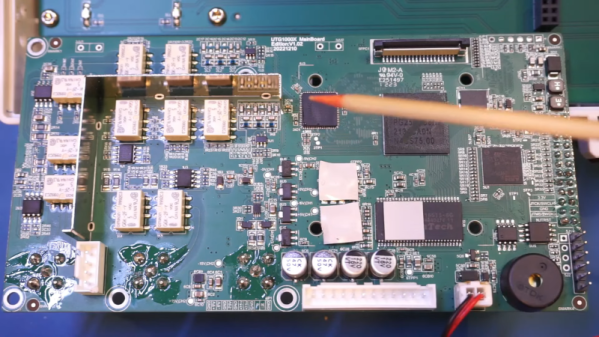
The power supply is unremarkable. There are a few odd output voltages. The main board is a bit more interesting, especially after removing the heat sink. There are two channels, but the board isn’t laid out, with a lot of segregation between the two channels. That makes sense with the output sections clustered together and the digital section with the CPU, FPGA, and the DAC in close proximity.
The other side of the board connects to a very simple display board. It would be interesting to compare this to a circa-1980s AWG, which would have been far more complicated.
Making a waveform generator with a microprocessor and a DAC isn’t hard. The hard part is the output stages and maximizing the operating speed.
Continue reading “Waveform Generator Teardown Is Nearly Empty”