Back in the old days, when we were still twiddling bits with magnetized needles, changing the data on an EPROM wasn’t as simple as shoving it in a programmer. These memory chips were erased with UV light shining through a quartz window onto a silicon die. At the time, there were neat little blacklights in a box sold to erase these chips. There’s little need for these chip erasers now, so how do you erase and program a chip these days? Build your own chip eraser using components that would have blown minds back in the 70s.
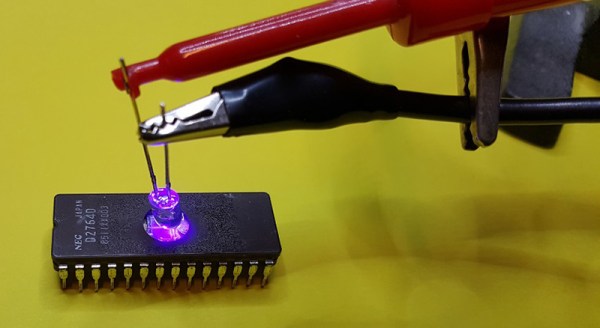
[Charles] got his hands on an old 2764 EPROM for a project, but this chip had a problem — there was still data on it. Fortunately, old electronics are highly resistant to abuse, so he pulled out the obvious equipment to erase this chip, a 300 watt tanning lamp. This almost burnt down the house, and after a second round of erasing of six hours under the lamp, there were still unerased bits.
Our ability to generate UV light has improved dramatically over the last fifty years, and [Charles] remembered he had an assortment of LEDs, including a few tiny 5mW UV LEDs. Can five milliwatts do what three hundred watts couldn’t? Yes; the LED had the right frequency to flip a bit, and erasing an EPROM is a function of intensity and time. All you really need to do is shine a LED onto a chip for a few hours.
With this vintage chip erased, [Charles] slapped together an EPROM programmer — with a programming voltage of 21V — out of an ATMega and a bench power supply. It eventually worked, allowing [Charles]’ project, a vintage liquid crystal display, to have the right data using vintage-correct parts.








 [Jolar] was working on
[Jolar] was working on 








