We’ve always been a little sad that supercapacitors aren’t marked with a big red S on a yellow background. Nevertheless, [DiodeGoneWild] picked up some large-value supercapacitors and used his interesting homemade oscilloscope to examine how they worked. You can watch what he is up to in his workshop in the video below.
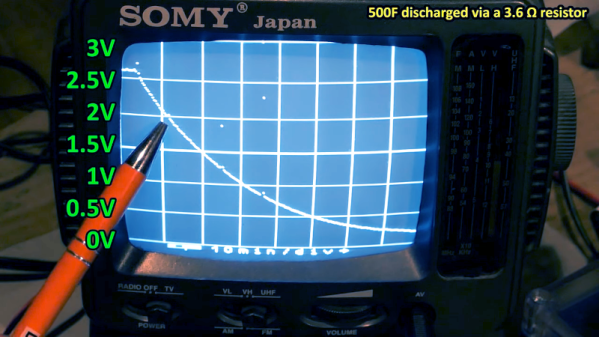
Supercapacitors use special techniques to achieve very high capacitance values. For example, the first unit in the video is a 500 F capacitor. That’s not a typo — not microfarads or even millifarads — a full 500 Farads. With reasonable resistance, it can take a long time to charge 500F, so it is easier to see the behavior, especially with the homemade scope, which probably won’t pick up very fast signals.
For example, A 350 mA charging current takes about an hour to bring the capacitor up to 2.6 V, just under its maximum rating of 2.7 V. Supercapacitors usually have low voltage tolerance. Their high capacity makes them ideal for low-current backup applications where you might not want a rechargeable battery because of weight, heat, or problems with long-term capacity loss.
The real star of the video, though, is the cast of homemade test equipment, including the oscilloscope, a power supply, and a battery analyzer. To be fair, he also has some store-bought test gear, too, and the results seem to match well.
Supercapacitors are one of those things that you don’t need until you do. If you haven’t had a chance to play with them, check out the video or at least watch it to enjoy the homebrew gear. We usually look to [Andreas Spiess] for ESP32 advice, but he knows about supercaps, too. If you really like making as much as you can, you can make your own supercapacitors.
Continue reading “Homemade Scope Does Supercapacitor Experiments”