Here’s a bulky tutorial that will round-out your understanding of ZigBee wireless communications (translated). The protocol is great for hobby electronics projects because it uses low-power short range wireless devices to build a mesh network. The guide covers both hardware and software, but also takes the time to explain what that hardware is doing in the background.
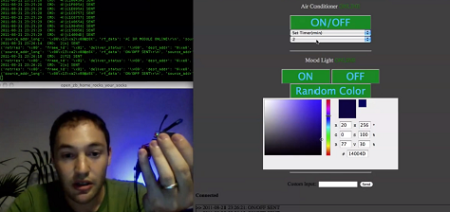
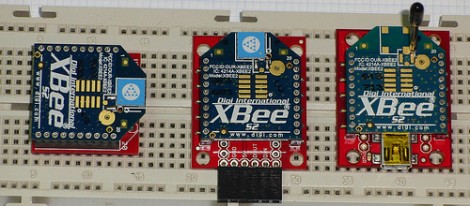
As you can see, several different renditions of an XBee module are used as examples. They pretty much all rely on a series of SparkFun breakout boards that each serve different purposes. Once you’ve acquired these modules, there’s a fair number of choices needed to configure them to play nicely with each other. We read most of the tutorial (we’ll save the rest for later enjoyment) and had no problem following along even without owning the hardware or being able to use the interface as we learned.
Whenever we cover XBee modules we always like to mention that it’s quite easy to use these for remote sensors with no additional microcontroller needed.