Recently [Glen Akins] reported on Bluesky that the Zigbee-based sensor he had made for his garden’s rear gate was still going strong after a Summer and Winter on the original 2450 lithium coin cell. The construction plans and design for the unit are detailed in a blog post. At the core is the MS88SF2 SoM by Minew, which features a Nordic Semiconductor nRF52840 SoC that provides the Zigbee RF feature as well as the usual MCU shenanigans.
Previously [Glen] had created a similar system that featured buttons to turn the garden lights on or off, as nobody likes stumbling blindly through a dark garden after returning home. Rather than having to fumble around for a button, the system should detect when said rear gate is opened. This would send a notification to [Glen]’s phone as well as activate the garden lights if it’s dark outside.
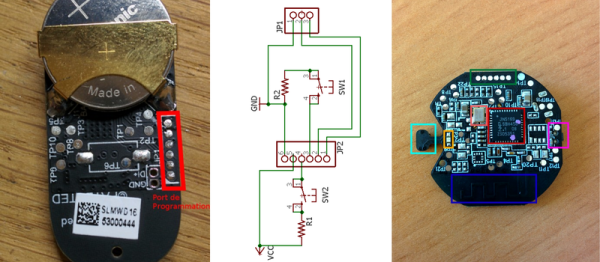
Although using a reed relay switch seemed like an obvious solution to replace the buttons, holding it closed turned out to require too much power. After looking at a few commercial examples, he settled for a Hall effect sensor solution with the Ti DRV5032FB in a TO-92 package.
Whereas the average person would just have put in a PIR sensor-based solution, this Zigbee solution does come with a lot more smart home creds, and does not require fumbling around with a smartphone or yelling at a voice assistant to turn the garden lights on.