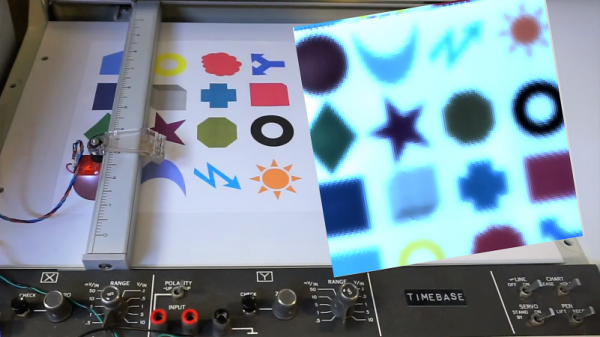
With so many ways to capture images from paper, do we really need another one? Especially one that takes 15 minutes to capture a 128×128 pixel image? Probably not, but building a single-pixel RGB scanner is pretty instructive, and good clean fun to boot.
We have to admit that when [Kerry Wong] scored an ancient Hewlett-Packard X-Y chart recorder a while back, we wondered if it would lead to anything useful. One may quibble with the claim that the Lorenz attractor plotter he built with it is useful, and this single pixel scanner is equally suspect, but we like the idea. Using an Arduino to drive the X- and X-axis of the recorder through a raster pattern over the bed and replacing the pen with an RGB sensor board, [Kerry] was able to collect the color data for each pixel and reconstruct the image. It wouldn’t be too hard to replicate this if you don’t have an analog X-Y recorder, which just goes to show that not everything needs to be steppers and digital to get something useful done. Or at least semi-useful.
As for the RGB sensor used, they’ve made appearances here many times before, mostly in M&M sorters but with the occasional synesthesia simulator.
Continue reading “Old Chart Recorder Becomes Single-Pixel Scanner”





 In the digital version of the game, the tokens conveniently display a number representing their total power value. [Martin] liked this feature, and set out to design a replacement token for the tabletop version that could display a number while still keeping the aesthetic of the originals. The tokens were designed as a dial with a small cutout window to show a number, but the surface of the token showing color and icon is still mostly unchanged.
In the digital version of the game, the tokens conveniently display a number representing their total power value. [Martin] liked this feature, and set out to design a replacement token for the tabletop version that could display a number while still keeping the aesthetic of the originals. The tokens were designed as a dial with a small cutout window to show a number, but the surface of the token showing color and icon is still mostly unchanged.









