More than three years have passed since Tesla announced its Cybertruck, and while not a one has been delivered, the first Tesla truck, Truckla, has kept on truckin’. [Simone Giertz] just posted an update of what Truckla has been up to since it was built.
[Giertz] and friend’s DIT (do-it-together) truck was something of an internet sensation when it was revealed several months before the official Tesla Cybertruck. As with many of our own projects, while it was technically done, it still had some rough edges that kept it from being truly finished, like a lack of proper waterproofing or a tailgate that didn’t fold.
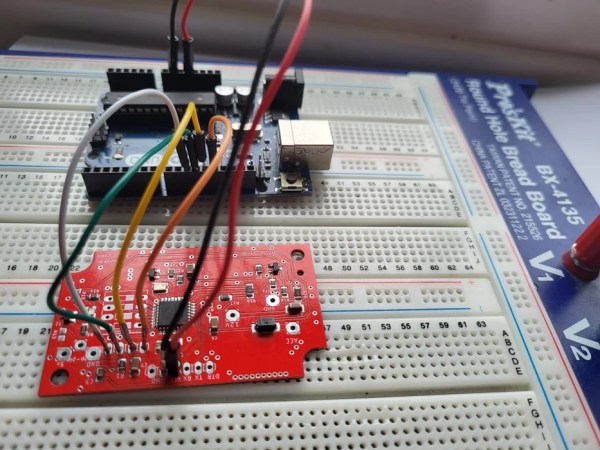
Deciding enough was enough, [Giertz] brought Truckla to [Marcos Ramirez] and [Ross Huber] to fix the waterproofing and broken tailgate while she went to [Viam Labs] to build Chargla, an Open Source charging bot for Truckla. The charging bot uses a linear actuator on a rover platform to dock with the charging port and is guided by a computer vision system. Two Raspberry Pis power handle the processing for the operation. We’re anxious to see what’s next in [Giertz]’s quest of “picking up the broken promises of the car world.”
If you want to see some more EV charger hacks, check out this Arduino-Based charger and the J1772 Hydra.
Continue reading “Truckla Gets An Open Source Charging Buddy”