Battlelines are being drawn in Canada over the lowly Flipper Zero, a device seen by some as an existential threat to motor vehicle owners across the Great White North. The story started a month or so ago, when someone in the government floated the idea of banning devices that could be “used to steal vehicles by copying the wireless signals for remote keyless entry.” The Flipper Zero was singled out as an example of such a nefarious device, even though relatively few vehicles on the road today can be boosted using the simple replay attack that a Flipper is capable of, and the ones that are vulnerable to this attack aren’t all that desirable — apologies to the 1993 Camry, of course. With that threat hanging in the air, the folks over at Flipper Devices started a Change.org petition to educate people about the misperceptions surrounding the Flipper Zero’s capabilities, and to urge the Canadian government to reconsider their position on devices intended to explore the RF spectrum. That last bit is important, since transmit-capable SDR devices like the HackRF could fall afoul of a broad interpretation of the proposed ban; heck, even a receive-only SDR dongle might be construed as a restricted device. We’re generally not much for petitions, but this case might represent an exception. “First they came for the Flipper Zero, but I did nothing because I don’t have a Flipper Zero…”
rolling code5 Articles
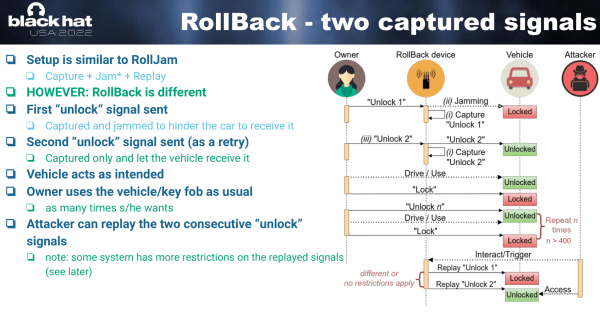
RollBack Breaks Into Your Car
Rolling codes change the signal sent by car keyfobs unpredictably on every use, rendering them safe from replay attacks, and we can all sleep well at night. A research team lead by [Levente Csikor] gave a presentation at Black Hat where they disclose that the situation is not pretty at all (PDF).
You might know [Samy Kamkar]’s RollJam attack, which basically consists of jamming the transmission between fob and car while the owner walks away, fooling the owner into clicking again, and then using one of the two rolling codes to lock up the car, keeping the other in your back pocket to steal it once they’re getting coffee. This is like that, but much, much worse. Continue reading “RollBack Breaks Into Your Car”
Unlock Any (Honda) Car
Honda cars have been found to be severely vulnerable to a newly published Rolling PWN attack, letting you remotely open the car doors or even start the engine. So far it’s only been proven on Hondas, but ten out of ten models that [kevin2600] tested were vulnerable, leading him to conclude that all Honda vehicles on the market can probably be opened in this way. We simply don’t know yet if it affects other vendors, but in principle it could. This vulnerability has been assigned the CVE-2021-46145.
[kevin2600] goes in depth on the implications of the attack but doesn’t publish many details. [Wesley Li], who discovered the same flaw independently, goes into more technical detail. The hack appears to replay a series of previously valid codes that resets the internal PRNG counter to an older state, allowing the attacker to reuse the known prior keys. Thus, it requires some eavesdropping on previous keyfob-car communication, but this should be easy to set up with a cheap SDR and an SBC of your choice.
If you have one of the models affected, that’s bad news, because Honda probably won’t respond anyway. The researcher contacted Honda customer support weeks ago, and hasn’t received a reply yet. Why customer support? Because Honda doesn’t have a security department to submit such an issue to. And even if they did, just a few months ago, Honda has said they will not be doing any kind of mitigation for “car unlock” vulnerabilities.
As it stands, all these Honda cars affected might just be out there for the taking. This is not the first time Honda is found botching a rolling code implementation – in fact, it’s the second time this year. Perhaps, this string of vulnerabilities is just karma for Honda striking down all those replacement part 3D models, but one thing is for sure – they had better create a proper department for handling security issues.
Hacker Claims Honda And Acura Vehicles Vulnerable To Simple Replay Attack
Keyless entry has become a standard feature on virtually all cars, where once it was a luxury option. However, it’s also changed the way that thieves approach the process of breaking into a car. After recent research, [HackingIntoYourHeart] claims that many modern Honda and Acura vehicles can be accessed with a simple replay attack using cheap hardware.
It’s a bold claim, and one that we’d love to see confirmed by a third party. The crux of the allegations are that simply recording signals from a Honda or Acura keyfob is enough to compromise the vehicle. Reportedly, no rolling code system is implemented and commands can easily be replayed.
Given these commands control features like unlocking the doors, opening the trunk, and even remote starting the vehicle, it’s a concerning situation. However, it’s also somewhat surprising. Rolling code technology has been around for decades, and makes basic replay attacks more difficult. Range extender attacks that target keyfobs sitting inside homes or gas stations are more common these days.
Whether Honda has made a security faux pas, or if there’s something more at play here, remains to be seen. If you’ve got more information, or have been able to recreate the same hack on your own Honda, be sure to let us know.
Executing A Vehicle Keyless Entry Attack
You read about well-publicised security exploits, but they always seem to involve somebody with a deity’s grasp of whatever technology is being employed, as well as a pile of impossibly exotic equipment. Surely a mere mortal could never do that!
Happily, that’s not always the case, and to prove it [Gonçalo Nespral] replicated an attack against RF devices such as some garage doors and motor vehicle locks that use a rolling code. His inspiration came from a device from2015, that encouraged the owner of a key to keep transmitting fresh codes. It did this by swamping the receiver of the car, garage door, or whatever with a strong slightly off frequency signal. This would cause the lock to not work, so the user would try again and again. The attacker listens with a very narrow bandwidth receiver on-frequency that is good enough to reject the jamming signal, and can harvest a sequence of the rolling codes enough to compromise it.
[Gonçalo]’s set-up uses a YARD stick One transceiver dongle as its transmitter, and an RTL-SDR for receive. A GNU Radio setup is used to retrieve the key data, and some custom Python code does the remaining work. We wouldn’t advocate using this in the wild and it could conceivably also gain you access to another car with a flashing light on top, but it’s an interesting exposé of the techniques involved.
Rolling code keyfob attacks are something we covered a few years ago, back when these attacks were all shiny and new.