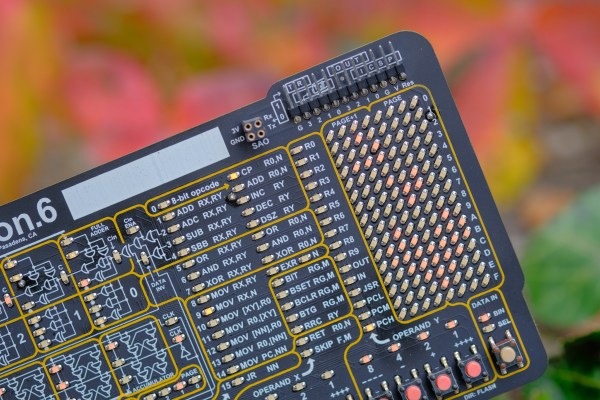
The inner orbits of the Hackaday solar system have been vibrating with the announcement of the 2022 Hackaday Supercon badge. The short version of the story is that it’s a “retrocomputer”. But I think that’s somehow selling it short a little bit. The badge really is an introduction to machine language or maybe a programming puzzle, a ton of sweet blinky lights and clicky buttons, and what I think of as a full-stack hacking invitation.
Voja Antonic designed the virtual 4-bit machine that lives inside. What separates this machine from actual old computers is that everything that you might want to learn about its state is broken out to an LED on the front face, from the outputs of the low-level logic elements that compose the ALU to the RAM, to the decoder LEDs that do double-duty as a disassembler. You can see it all, and this makes it an unparalleled learning aid. Or at least it gives you a fighting chance.
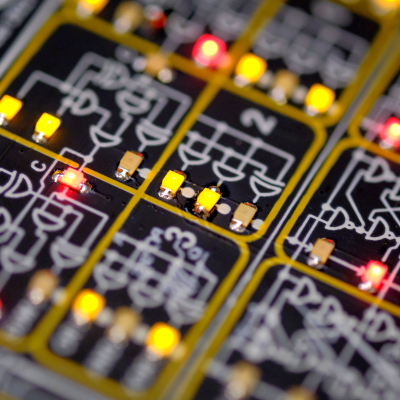 So why would you want to learn a made-up machine language from a non-existent CPU? Tom Nardi and I were talking about our experiences on the podcast, and we both agreed that there’s something inexplicably magical about flipping bits, calling the simplest of computer operations into action, and nonetheless making it do your bidding. Or rather, it’s anti-magical, because what’s happening is the stripping away of metaphors and abstractions. Peering not just behind, but right through the curtain. You’re seeing what’s actually happening for once, from the bottom to the top.
So why would you want to learn a made-up machine language from a non-existent CPU? Tom Nardi and I were talking about our experiences on the podcast, and we both agreed that there’s something inexplicably magical about flipping bits, calling the simplest of computer operations into action, and nonetheless making it do your bidding. Or rather, it’s anti-magical, because what’s happening is the stripping away of metaphors and abstractions. Peering not just behind, but right through the curtain. You’re seeing what’s actually happening for once, from the bottom to the top.
As Voja wrote on the silkscreen on the back of the badge itself: “A programmer who has never coded 1s and 0s in machine language is like a child who has never run barefoot on the grass.” It’s not necessary, or maybe even relevant, but learning a complex machine in its entirety is simultaneously grounding and mind-expanding. It is simply an experience that you should have.