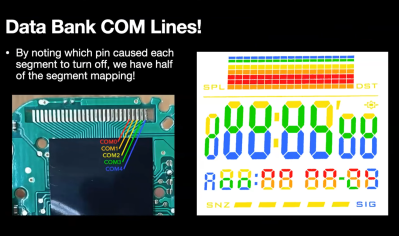
Started by graduate students from the California Institute of Technology in the late 1930s, the Jet Propulsion Laboratory (JPL) was instrumental in the development of early rocket technology in the United States. After being tasked by the Army to analyze the German V2 in 1943, the JPL team expanded from focusing purely on propulsion systems to study and improve upon the myriad of technologies required for spaceflight. Officially part of NASA since December of 1958, JPL’s cutting edge research continues to be integral to the human and robotic exploration of space.
For longtime friend of Hackaday Ara “Arko” Kourchians, getting a job JPL as a Robotics Electrical Engineer was a dream come true. Which probably explains why he applied more than a dozen times before finally getting the call to join the team. He stopped by the Hack Chat back in August of 2019 to talk about what it’s like to be part of such an iconic organization, reminisce about some of his favorite projects, and reflect on the lessons he’s learned along the way.
Continue reading “Classic Chat: Arko Takes Us Inside NASA’s Legendary JPL”