As the art of 3D printing has refined itself over the years, a few accessories have emerged to take prints to the next level. One of them is the threaded insert, a a piece of machined brass designed to be heat-set into a printed hole in the part. They can be placed by hand with a soldering iron, or for the really cool kids, with a purpose-built press. They look great and they can certainly make assembly of a 3D printed structure very easy, but I’m here to tell you they are not as necessary as they might seem. There’s an alternative I have been using for years which does essentially the same job without the drama. Continue reading “No Need For Inserts If You’re Prepared To Use Self-Tappers”
Hackaday Columns4669 Articles
This excellent content from the Hackaday writing crew highlights recurring topics and popular series like Linux-Fu, 3D-Printering, Hackaday Links, This Week in Security, Inputs of Interest, Profiles in Science, Retrotechtacular, Ask Hackaday, Teardowns, Reviews, and many more.
Hackaday Links: August 31, 2025
Back in March, we covered the story of Davis Lu, a disgruntled coder who programmed a logic bomb into his employers’ systems. His code was malicious in the extreme, designed as it was to regularly search for his Active Directory entry and fire off a series of crippling commands should it appear he had been fired. His 2019 sacking and subsequent deletion of his AD profile triggered the job, wreaking havoc on servers and causing general mayhem. Whatever satisfaction Lu drew from that must have been fleeting, because he was quickly arrested, brought to trial in federal court, and found guilty of causing intentional damage to protected computer systems.
Lu faced a decade in federal prison for the stunt, but at his sentencing last week, he got four years behind bars followed by three years of supervised release. That’s still a pretty stiff sentence, and depending on where he serves it, things might not go well for him. Uber-geek Chris Boden has some experience in the federal prison system as a result of some cryptocurrency malfeasance; his video on his time in lockup is probably something Mr. Lu should watch while he can. Honestly, we feel bad for him in a way because we’ve been there; we certainly toyed with the logic bomb idea when we were coding for a living, without actually ever doing it. Maybe he thought it would just get treated as a prank, but that was probably never in the cards; as we’re fond of telling our kids, the world just doesn’t have a sense of humor anymore.
Hackaday Podcast Episode 335: Beer, Toast, And Pi
What happens when you listen in on Elliot Williams and Al Williams? You get a round up of the best of last week’s Hackaday posts, of course. The topics this week range from beer brewing to lightning protection, with a little bit of everything in between.
This week, many problems find solutions. Power drill battery dead? Your car doesn’t have a tire pressure monitor? Does your butter tear up your toast? You can find the answer to these problems, and more, on the Hackaday podcast.
For the can’t miss section, the guys are annoyed that Google wants to lock down their phones, and also talk about measuring liquid levels in outer space.
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
Or download in DRM-free MP3 without requiring developer registration.
Continue reading “Hackaday Podcast Episode 335: Beer, Toast, And Pi”
This Week In Security: DEF CON Nonsense, Vibepwned, And 0-days
DEF CON happened just a few weeks ago, and it’s time to cover some of the interesting talks. This year there were two talks in particular that are notable for being controversial. Coincidentally both of these were from Track 3. The first was the Passkeys Pwned, a talk by SquareX about how the passkey process can be hijacked by malware.
[Dan Goodin] lays out both the details on Passkeys, and why the work from SquareX isn’t the major vulnerability that they claim it is. First, what is a Passkey? Technically it’s a public/private keypair that is stored by the user’s browser. A unique keypair is generated for each new website, and the site stores the public key. To authenticate with the Passkey, the site generates a random string, the browser signs it with the private key, and the site checks it against the public key. I stand by my early opinion, that Passkeys are effectively just passwords, but with all the best-practices mandated.
So what is the claim presented at DEF CON? Malicious code running in the context of the browser tab can hijack the passkey process. In the demonstrated attack flow, a browser extension caused the Passkey login to fail, and prompted the user to generate a new Passkey. This is an interesting observation, and a clever attack against Passkeys, but is not a vulnerability in the Passkey spec. Or more accurately, it’s an accepted limitation of Passkeys, that they cannot guarantee security in the presence of a compromised browser. Continue reading “This Week In Security: DEF CON Nonsense, Vibepwned, And 0-days”
FLOSS Weekly Episode 844: Simulated Word-of-Mouth
This week Jonathan, Doc, and Aaron chat about Open Source AI, advertisements, and where we’re at in the bubble roller coaster!
Continue reading “FLOSS Weekly Episode 844: Simulated Word-of-Mouth”
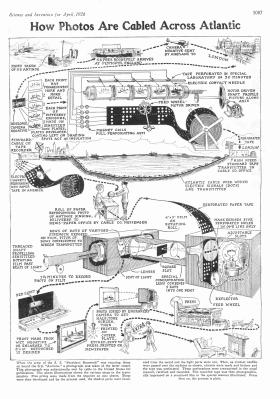
Picture By Paper Tape
Of course, the answer is analog fax. But think about it. How would you create an analog fax machine in 1926? The graphic is quite telling. (Click on it to enlarge, you won’t be disappointed.)
If you are like us, when you first saw it you thought: “Oh, sure, paper tape.” But a little more reflection makes you realize that solves nothing. How do you actually scan the photo onto the paper tape, and how can you reconstitute it on the other side? The paper tape is clearly digital, right? How do you do an analog-to-digital converter in 1926? Continue reading “Picture By Paper Tape”
Debugging The Instant Macropad
Last time, I showed you how to throw together a few modules and make a working macropad that could act like a keyboard or a mouse. My prototype was very simple, so there wasn’t much to debug. But what happens if you want to do something more complex? In this installment, I’ll show you how to add the obligatory blinking LED and, just to make it interesting, a custom macro key.
There is a way to print data from the keyboard, through the USB port, and into a program that knows how to listen for it. There are a few choices, but the qmk software can do it if you run it with the console argument.
The Plan
In theory, it is fairly easy to just add the console feature to the keyboard.json file:
{
...
"features": {
"mousekey": true,
"extrakey": true,
"nkro": false,
"bootmagic": false,
"console": true
},
...
That allows the console to attach, but now you have to print.