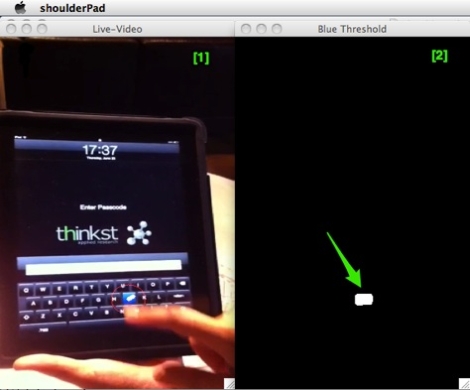
A pair of security researchers have recently unveiled an interesting new keylogging method (PDF Research Paper) that makes use of a very unlikely smartphone component, your gyroscope.
Most smart phones now come equipped with gyroscopes, which can be accessed by any application at any time. [Hao Chen and Lian Cai] were able to use an Android phone’s orientation data to pin down what buttons were being pressed by the user. The attack is not perfect, as the researchers were only able to discern the correct keypress about 72% of the time, but it certainly is a good start.
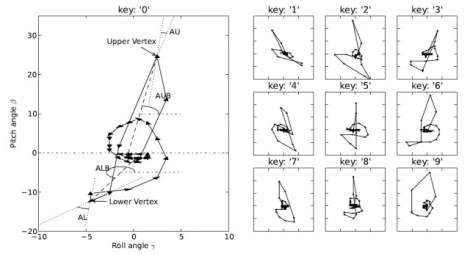
This side channel attack works because it turns out that each button on a smart phone has a unique “signature”, in that the phone will consistently be tilted in a certain way with each keypress. The pair does admit that the software becomes far less accurate when working with a full qwerty keyboard due to button proximity, but a 10 digit pad and keypads found on tablets can be sniffed with relatively good results.
We don’t think this is anything you should really be worried about, but it’s an interesting attack nonetheless.
[Thanks, der_picknicker]