We’ve all heard of those chirper devices that randomly make annoying noises for no other reason than sending people insane. This project from [Kousuke Saito] brings altogether more art to this idea, while still being quite annoying indeed.
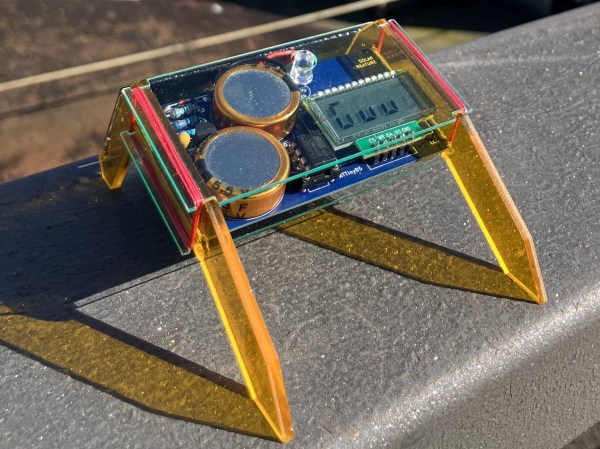
The build is essentially a replica cicada. [Saito] was inspired to build the device as the sounds of the insect remind him fondly of the summer. His design consists of a 3D-printed housing that roughly approximates something like a cicada, with two wings attached to a central body. In this case, the layer lines of the 3D print actually added to the realism of the ersatz insect The housing is nicely painted to serve as an adequate simulacra to those who aren’t up on their entomology.
Inside, there’s an ATTiny 85 paired with an MP3 playback module and a small speaker. It’s charged with reproducing the noise of various cicadas. It’s setup with an ingenious mechanism to switch it on. There are magnets installed in the base which allow it to stick to metallic objects. There’s also a switch in the bottom of the device. When it magnetically attaches to a surface, that switch is depressed, and the cicada starts playing, well… cicada noises. [Saito] notes that a patent has been secured for the idea.
We’ve seen other cicada-themed projects before, astoundingly. Video after the break.
Continue reading “Annoying Cicada Magnet Is Nonetheless Authentic”