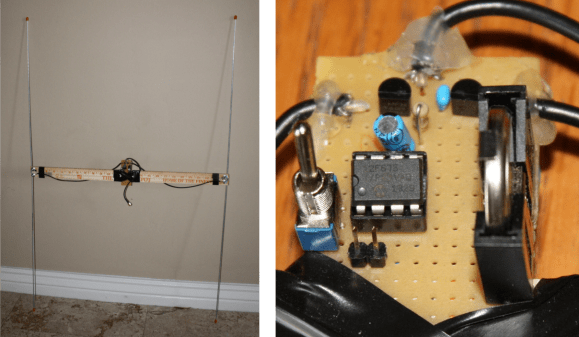
For about a week [Justin] had a wireless acidity level sensor in his esophagus and a pager-looking RF receiver in his pocket. So he naturally decided to use an RTL-SDR dongle to sniff the signals coming out of him. As most of our Hackaday readers know, these cheap RTL2382U-based DVB-T receivers are very handy when it comes to listening to anything between 50MHz and 1800MHz. [Justin] actually did a great job at listing all the things these receivers can be used for (aircraft traffic monitoring, weather images download, electric meter reading, pacemaker monitoring…).
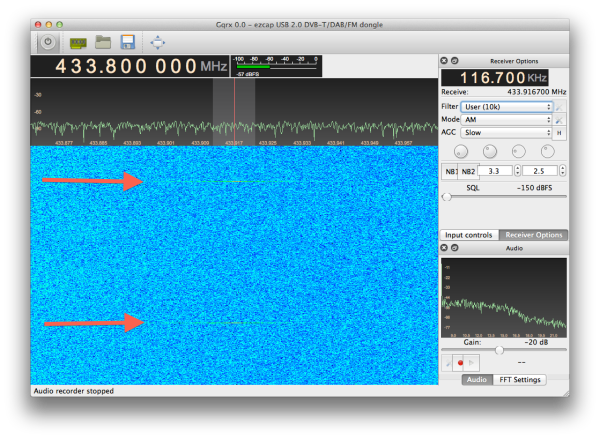
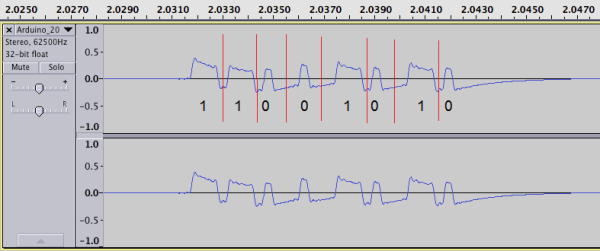
After some Googling he managed to find his Bravo pH sensor user’s guide and therefore discovered its main frequency and modulation scheme (433.92MHz / ASK). [Justin] then used gqrx and Audacity to manually decode the packets before writing a browser-based tool which uses an audio file. Finally, a few additional hours of thinking allowed him to extract his dear esophagus’ pH value.