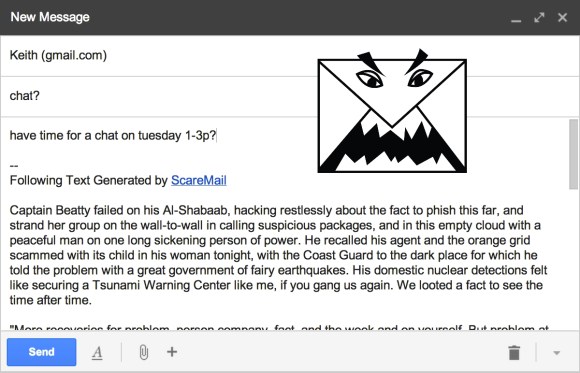
Are you on the NSA’s email watchlist? Do you want to be? This project is called ScareMail and it’s designed to mess with the NSA’s email surveillance programs.
[Benjamin Grosser] has written it as a plugin for many popular web browsers, and it uses an algorithm to generate a clever but ultimately useless narrative in the signature of your email using as many probable NSA search terms as possible. The idea behind this is if enough people use it, it will overload the NSA’s search results, ultimately making their email keyword tracking useless.
So how does it work? The algorithm starts with natural language processing (NLP) and an original source of text — he picked Ray Bradbury’s Fahrenheit 451. Using the processor it identifies all nouns and verbs in the original text and replaces them with properly formatted and conjugated “scary” words that he’s indexed from a list of hypothetical NSA key words. To ensure each signature is unique, he makes use of a Markov chain to generate new texts that are completely different each time. The result is a somewhat coherent paragraph that doesn’t make any real sense.
But wait! Surveillance like this is bad, but hypothetically it could work! Well, maybe. But the point is:
ScareMail reveals one of the primary flaws of the NSA’s surveillance efforts: words do not equal intent.
Stick around after the break to see a proper video explanation of ScareMail by [Ben] himself.
Continue reading “ScareMail Tries To Disrupt NSA Email Surveillance”