The invention of sprites triggered a major shift in video game design, enabling games with independent moving objects and richer graphics despite the limitations of early video gaming hardware. As a result, hardware design was specifically built to manipulate sprites, and generally as new generations of hardware were produced the number of sprites a system could produce went up. But [Coding Secrets], who published games for the Commodore Amiga, used an interesting method to get this system to produce far more sprites at a single time than the hardware claimed to support.
This hack is demonstrated with [Coding Secrets]’s first published game on the Amiga, Leander. Normally the Amiga can only display up to eight sprites at once, but there is a coprocessor in the computer that allows for re-drawing sprites in different areas of the screen. It can wait for certain vertical and horizontal line positions and then execute certain instructions. This doesn’t allow unlimited sprites to be displayed, but as long as only eight are displayed on any given line the effect is similar. [Coding Secrets] used this trick to display the information bar with sprites, as well as many backgrounds, all simultaneously with the characters and enemies we’d normally recognize as sprites.
Of course, using built-in hardware to do something the computer was designed to do isn’t necessarily a hack, but it does demonstrate how intimate knowledge of the system could result in a much more in-depth and immersive experience even on hardware that was otherwise limited. It also wasn’t free to use this coprocessor; it stole processing time away from other tasks the game might otherwise have to perform, so it did take finesse as well. We’ve seen similar programming feats in other gaming projects like this one which gets Tetris running with only 1000 lines of code.
Continue reading “The Many-Sprites Interpretation Of Amiga Mechanics”



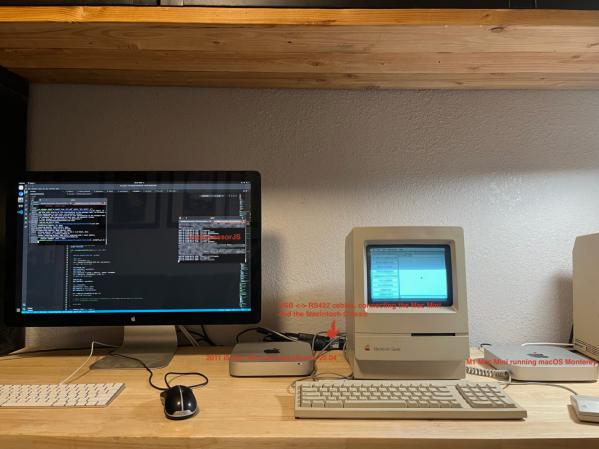
 Unfortunately, it does require a more modern Mac to act as an access point into the wider iMessage network. The modern Mac sets up a GraphQL database that can be accessed. Then a serial cable connects your “retro daily driver” to a translation layer that converts the serial commands into GraphQL commands. This could be something simple and network-connected like an ESP32 or a program running on your iMessage Mac. [CamHenlin] has a second Mac mini in his demo, seen above.
Unfortunately, it does require a more modern Mac to act as an access point into the wider iMessage network. The modern Mac sets up a GraphQL database that can be accessed. Then a serial cable connects your “retro daily driver” to a translation layer that converts the serial commands into GraphQL commands. This could be something simple and network-connected like an ESP32 or a program running on your iMessage Mac. [CamHenlin] has a second Mac mini in his demo, seen above.