There are a couple of really great things about transmitting data using light as the carrier. It can be focused so that it doesn’t spill all over the neighborhood like radio signals do — giving it both some security against eavesdropping and preventing one signal from stepping on another’s toes. And while you can modulate radio signals up nearly to the carrier frequency, the few gigahertz we normally use for radio just won’t cut it for really high bit rates. Light gets you terahertz.
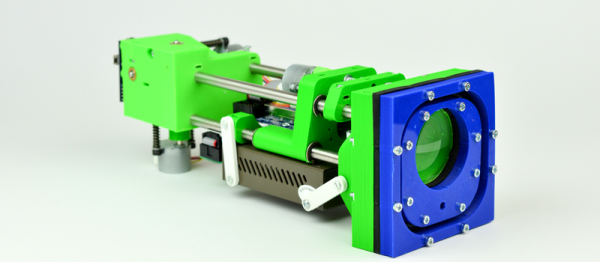
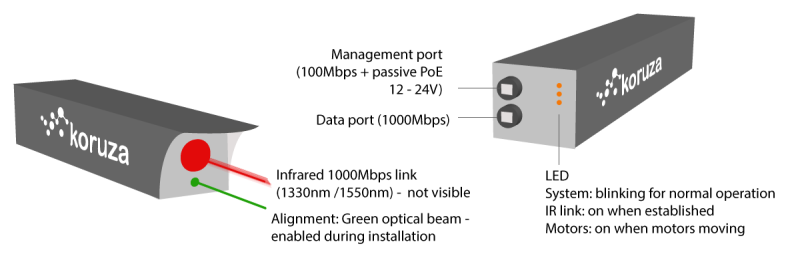
The Koruza project is an open-source, “inexpensive” system that aims to transmit 1 Gb/sec over distances around 100 meters, using modulated infrared light. The intended use-case is urban building-to-building communication at speeds that would otherwise require laying fiber-optic cables. Indeed, the system piggy-backs on existing fiber-optic equipment to get the job done, but the hard part is aligning the units to get maximum signal from point A to point B.
Koruza does this by including motorized lenses on the 3D-printed chassis. You make a rough alignment with a visible green laser, and then fine-tune the IR beams from a web console where you get immediate feedback on how the received signal strength is changing. Both Koruza boxes have a Raspberry Pi inside and use normal networking for calibration and signal-strength statistics. It’s a really neat system, and it’s fully DIY’able except for the commodity fiber-optic bits.
We’ve always had a soft-spot in our heart for transmitting data over light beams. The Ronja project has been doing so since 2001, and over longer distances, with completely DIY hardware, if at a slower bitrate. And now that Li-Fi seems to be getting traction, we might see an unfocused equivalent running inside our homes.
Thanks [Pavel] for the tip!