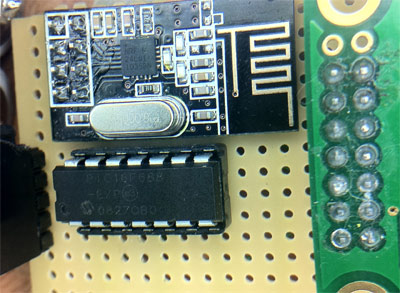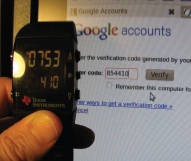
Two-factor authentication allows you to use your chosen password, as well as a one-time password to help keep your services secure. The one-time passwords traditionally come from a dedicated piece of hardware, but there are also solutions for smart phones. [Patrick Schaumont] shows how a TI eZ430 Chronos Watch can be used to generate authentication tokens. After walking through the process he uses it to beef up his gmail login.
This method of token authentication is often called Time-based One Time Passwords (TOTP). It’s part of the Open Authentication (OATH) initiative, which seeks to sort out the password-hell that is modern computing. A portable device generates a password by applying an algorithm and a private encryption key to an accuarte time-stamp. On the server side of things a public key is used to verify the one-time password entered based on the server’s own time-stamp. In this case the portable device is the Chronos watch and the server is Google’s own TOTP service.
You can do this with other simple microcontrollers, we’ve even seen an Arduino implementation. But the wrist-watch form factor seen here is by far the most convenient — as long as you always remember to wear the watch.
[Thanks Oxide]