It’s been a busy week in space news, and very little of it was good. We’ll start with the one winner of the week, Firefly’s Blue Ghost Mission 1, which landed successfully on the Moon’s surface on March 2. The lander is part of NASA’s Commercial Lunar Payload Services program and carries ten scientific payloads, including a GPS/GNSS receiver that successfully tracked signals from Earth-orbiting satellites. All of the scientific payloads have completed their missions, which is good because the lander isn’t designed to withstand the long, cold lunar night only a few days away. The landing makes Firefly the first commercial outfit to successfully soft-land something on the Moon, and being the first at anything is always a big deal.
firmware161 Articles
Supercon 2024: Joshua Wise Hacks The Bambu X1 Carbon
Bambu Labs have been in the news lately. Not because of the machines themselves, but because they are proposing a firmware change that many in our community find restricts their freedom to use their own devices.
What can be done? [Joshua Wise] gave a standout talk on the Design Lab stage at the 2024 Hackaday Superconference where he told the tale of his custom firmware for the Bambu X1 Carbon. He wasn’t alone here; the X1 Plus tale involves a community of hackers working on opening up the printer, but it’s also a tale that hasn’t ended yet. Bambu is striking back. Continue reading “Supercon 2024: Joshua Wise Hacks The Bambu X1 Carbon”
Custom Firmware Adds Capabilities To Handie Talkie
Although ham radio can be an engaging, rewarding hobby, it does have a certain reputation for being popular among those who would fit in well at gated Florida communities where the preferred mode of transportation is the golf cart. For radio manufacturers this can be a boon, as this group tends to have a lot of money and not demand many new features in their technology. But for those of us who skew a bit younger, there are a few radios with custom firmware available that can add a lot of extra capabilities.
The new firmware is developed by [NicSure] for the Tidradio TD-H3 and TD-H8 models and also includes a browser-based utility for flashing it to the radio without having to install any other utilities. Once installed, users of these handheld radios will get extras like an improved S-meter and detection and display of CTCSS tones for repeater usage. There’s also a programmer available that allows the radio’s memory channels to be programmed easily from a computer and a remote terminal of sorts that allows the radio to be operated from the computer.
One of the latest firmware upgrades also includes a feature called Ultra Graph which is a live display of the activity on a selected frequency viewable on a computer screen. With a radio like this and its upgraded firmware, a lot of the capabilities of radios that sell for hundreds of dollars more can be used on a much more inexpensive handheld. All of this is possible thanks to an on-board USB-C interface which is another feature surprisingly resisted by other manufacturers even just for charging the batteries.
Continue reading “Custom Firmware Adds Capabilities To Handie Talkie”
Hackaday Links: December 22, 2024
Early Monday morning, while many of us will be putting the finishing touches — or just beginning, ahem — on our Christmas preparations, solar scientists will hold their collective breath as they wait for word from the Parker Solar Probe’s record-setting passage through the sun’s atmosphere. The probe, which has been in a highly elliptical solar orbit since its 2018 launch, has been getting occasional gravitational nudges by close encounters with Venus. This has moved the perihelion ever closer to the sun’s surface, and on Monday morning it will make its closest approach yet, a mere 6.1 million kilometers from the roiling photosphere. That will put it inside the corona, the sun’s extremely energetic atmosphere, which we normally only see during total eclipses. Traveling at almost 700,000 kilometers per hour, it won’t be there very long, and it’ll be doing everything it needs to do autonomously since the high-energy plasma of the corona and the eight-light-minute distance makes remote control impossible. It’ll be a few days before communications are re-established and the data downloaded, which will make a nice present for the solar science community to unwrap.
Unexpectedly Interesting Payphone Gives Up Its Secrets
Reverse engineering a payphone doesn’t sound like a very interesting project, at least in the United States, where payphones were little more than ruggedized versions of residential phones with a coin mechanism attached. Phones in other parts of the world were far more interesting, though, as this look at the mysteries of a payphone from Israel reveals (in Hebrew; English translation here.)
This is a project [Inbar Raz] worked on quite a while ago, but only got around to writing up recently. The payphone in question was sourced from the usual surplus market channels, and appears to have been removed from service by Israeli telecommunications company Bezeq only shortly before he found it. It was in pretty good shape, and was even still locked tight, making some amateur locksmithing the first order of the day. The internals of the phone are surprisingly complex, with a motherboard that looks more like something from a PC. Date codes on the chips and through-hole construction date the device to the early- to mid-1990s.
With physical access gained, [Inbar] turned to the firmware. An Atmel flash chip seemed a good place to look, and indeed he was able to pull code off the chip. That’s where things took a turn thanks to the CPU the code was written for — the CDP1806, a later version of the more popular but still fringe CDP1802. This required [Inbar] to fall down the rabbit hole of writing a new processor definition file for Ghidra so that the firmware could be reverse-engineered. This got him to the point of understanding 1806 assembly well enough that he was able to re-flash the phone to print debugging messages on the built-in 16×2 LCD screen, which allowed him to figure out which routines were being called under various error conditions.
It doesn’t appear that [Inbar] ever completed the reverse engineering project, but as he points out, what does that even mean? He got inside, took a look around, and made the phone do some cool things it couldn’t do before, and in the process made things easier for anyone working with 1806 processors in Ghidra. That’s a pretty complete win in our books.
Saving A Samsung TV From The Dreaded Boot Loop
[eigma] had a difficult problem. After pulling a TV out of the trash and bringing it home, it turned out it was suffering from a troubling boot loop issue that basically made it useless. As so many of us do, they decided to fix it…which ended up being a far bigger task than initially expected.
The TV in question was a Samsung UN40H5003AF. Powering it up would net a red standby light which would stay on for about eight seconds. Then it would flicker off, come back on, and repeat the cycle. So far, so bad. Investigation began with the usual—checking the power supplies and investigating the basics. No easy wins were found. A debug UART provided precious little information, and schematics proved hard to come by.
Eventually, though, investigation dialed in on a 4 MB SPI flash chip on the board. Dumping the chip revealed the firmware onboard was damaged and corrupt. Upon further tinkering, [eigma] figured that most of the dump looked valid. On a hunch, suspecting that maybe just a single bit was wrong, they came up with a crazy plan: use a script to brute-force flipping every single bit until the firmware’s CRC check came back valid. It took eighteen hours, but the script found a valid solution. Lo and behold, burning the fixed firmware to the TV brought it back to life.
It feels weird for a single bit flip to kill an entire TV, but this kind of failure isn’t unheard of. We’ve seen other dedicated hackers perform similar restorations previously. If you’re out there valiantly rescuing e-waste with these techniques, do tell us your story, won’t you?
Zero To Custom MacroPad In 37 Easy Steps
[Jeremy Weatherford] clearly has a knack for explaining projects well enough for easy reproduction but goes way further than most and has created a four-part YouTube series detailing every step from project inception to the final assembly, covering all aspects of 3D modelling and PCB design for a custom MacroPad design. Many tools are introduced along the way, all of which help reduce complexity and, by extension, the scope for errors. As every beginner hacker knows, early successes breed confidence and make for better and more ambitious projects.
Part 1 covers the project motivation and scope and introduces a keyboard layout editor tool. This tool allows one to take a layout idea and generate a JSON file, which is then used to drive keyboard tools. XYZ to produce a usable KiCAD project. The tool only generates a PCB project and an associated netlist file. No schematic is created; you don’t need one for a simple layout.
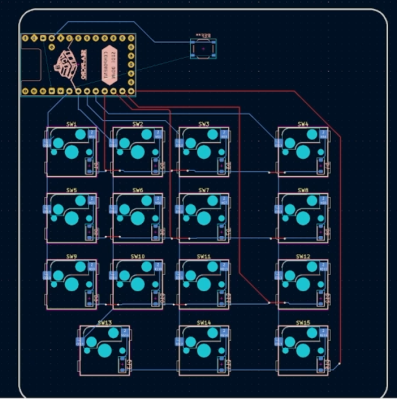
Part 2 is a walkthrough of the design process in KiCAD, culminating in ordering the PCB from JLCPCB and assembling the surface-mount parts. This particular design uses a controller based on the Sea-Picro RP2040 module, but there are many options if you have other preferences. [Jeremy] shows what’s possible with the selected suppliers, but you need not follow this step precisely if you have other ideas or want to use someone local.
Part 3 covers exporting the mechanical aspects of the PCB out of KiCAD and into a 3D CAD program, specifically OnShape. [Jeremy] covers some crucial details, such as how to read the mechanical drawing of the keys to work out where to place the top plate. It’s very easy to plough straight in at this stage and make a design which cannot be assembled! The plan is to use a simple laser-cut box with a bottom plate with mounting holes lining up with those on the PCB. A Top plate is created by taking the outline of the PCB and adding a little margin. An array of rectangular cutouts are designed for the keys to protrude, lining up perfectly with where the keys would be when mounted on the PCB below. The sides of the case are formed from laser-cut sections that lock into each other and the laser-cut base—using the laser joint feature-script addon tool from the OnShape community channel. A second feature script addon is used to auto-layout the laser-cut components onto a single sheet. A CAM application called Kiri Moto is used to export for laser cutting and is available on the OnShape store.
















