Battlelines are being drawn in Canada over the lowly Flipper Zero, a device seen by some as an existential threat to motor vehicle owners across the Great White North. The story started a month or so ago, when someone in the government floated the idea of banning devices that could be “used to steal vehicles by copying the wireless signals for remote keyless entry.” The Flipper Zero was singled out as an example of such a nefarious device, even though relatively few vehicles on the road today can be boosted using the simple replay attack that a Flipper is capable of, and the ones that are vulnerable to this attack aren’t all that desirable — apologies to the 1993 Camry, of course. With that threat hanging in the air, the folks over at Flipper Devices started a Change.org petition to educate people about the misperceptions surrounding the Flipper Zero’s capabilities, and to urge the Canadian government to reconsider their position on devices intended to explore the RF spectrum. That last bit is important, since transmit-capable SDR devices like the HackRF could fall afoul of a broad interpretation of the proposed ban; heck, even a receive-only SDR dongle might be construed as a restricted device. We’re generally not much for petitions, but this case might represent an exception. “First they came for the Flipper Zero, but I did nothing because I don’t have a Flipper Zero…”
flipper zero17 Articles
An Automotive Locksmith On The Flipper Zero And Car Theft
Here in the hacker community there’s nothing we love more than a clueless politician making a fool of themselves sounding off about a technology they know nothing about. A few days ago we were rewarded in spades by the Canadian Minister of Innovation, Science and Industry François-Philippe Champagne, who railed against the Flipper Zero, promising to ban it as a tool that could be used to gain keyless entry to a vehicle.
Of course our community has roundly debunked this assertion, as capable though the Flipper is, the car industry’s keyless entry security measures are many steps ahead of it. We’ve covered the story from a different angle before, but it’s worth returning to it for an automotive locksmith’s view on the matter from [Surlydirtbag].
He immediately debunks the idea of the Flipper being used for keyless entry systems, pointing out that thieves have been using RF relay based attacks which access the real key for that task for many years now. He goes on to address another concern, that the Flipper could be used to clone the RFID chip of a car key, and concludes that it can in the case of some very old vehicles whose immobilizers used simple versions of the technology, but not on anything recent enough to interest a car thief.
Of course, to many readers this will not exactly be news. But it’s still important, because perhaps some of us will have had to discuss this story with non-technical people who might be inclined to believe such scare stories. Being able to say “Don’t take it from me, take it from an automotive locksmith” might just help. Meanwhile there is still the concern of CAN bus attacks to contend with, something the manufacturers could have headed off had they only separated their on-board subsystems.
Continue reading “An Automotive Locksmith On The Flipper Zero And Car Theft”
Why Stealing A Car With Flipper Zero Is A Silly Idea
In another regular installment of politicians making ridiculous statements about technology, Canada’s Minister of Innovation, Science and Industry, [François-Philippe Champagne], suggested banning Flipper Zero and similar devices from sale in the country, while accusing them of being used for ‘stealing cars’ and similar. This didn’t sit right with [Peter Fairlie] who put together a comprehensive overview video of how car thieves really steal cars. Perhaps unsurprisingly, the main method is CAN bus injection, for which a Flipper Zero is actually a terribly clumsy device. Rather you’d use a custom piece of kit that automates the process.
You can also find these devices being sold all over the internet as so-called ‘Emergency Start’ devices for sale all over the internet, all of which use weaknesses in the car’s CAN bus network. The common problem appears to be that with these days even the lights on the car being part of the CAN network, an attacker can gain access for injection purposes. This way no key fob is needed, and the ignition system can be triggered with the usual safeties and lockouts being circumvented.
Ultimately, although the Flipper Zero is a rather cutesy toy, it doesn’t do anything that cannot be done cheaper and more effectively by anyone with a bit of CAN bus knowledge and a disregard for the law.
Thanks to [Stephen Walters] for the tip.
Continue reading “Why Stealing A Car With Flipper Zero Is A Silly Idea”
Canada Bans Flipper Zero Over What It Imagines It Does
Canada’s intent to ban the Flipper Zero wireless tool over car thefts is, on the one hand, an everyday example of poorly researched government action. But it may also be a not-so-subtle peek into the harm misinformation online can cause by leading to said government action.
The Government of Canada recently hosted a national summit on combatting vehicle theft, and Minister of Innovation, Science and Industry François-Philippe Champagne proudly declared immediate actions being taken to ban devices used to steal vehicles by wirelessly bypassing keyless entry, the Flipper Zero being specifically named as one such device.
And yet, defeating a rolling code keyless entry system is a trick a device like the Flipper Zero simply cannot pull off. (What cars have such a system? Any car made in roughly the last thirty years, for a start.)
Continue reading “Canada Bans Flipper Zero Over What It Imagines It Does”
IoT Air Purifier Makes A Great Case Study In Reverse Engineering
Here at Hackaday, about the only thing we like more than writing up tales of reverse engineering heroics is writing up tales of reverse engineering heroics that succeed in jailbreaking expensive widgets from their needless IoT dependency. It’s got a real “stick it to the man” vibe that’s hard to resist.
The thing is, we rarely see a reverse engineering write-up as thorough as the one [James Warner] did while integrating an IoT air purifier into Home Assistant, so we just had to make sure we called this one out. Buckle up; it’s a long, detailed post that really gets down into the weeds, but not unnecessarily so. [James] doesn’t cloud-shame the appliance manufacturer, so we can’t be sure who built this, but it’s someone who thought it’d be a swell idea to make the thing completely dependent on their servers for remote control via smartphone. The reverse engineering effort started with a quick look at the phone app, but when that didn’t pay off in any useful way, [James] started snooping on what the device was talking about using Wireshark.
One thing led to another, wires were soldered to the serial pins on the ESP32 on the purifier’s main board, and with the help of a FlipperZero as a UART bridge, the firmware was soon in hand. This gave [James] clues about the filesystem, which led to a whole Ghidra side quest into learning how to flash the firmware. [James] then dug into the meat of the problem: figuring out the packet structure used to talk to the server, and getting the private key used to encrypt the packets. This allowed a classic man-in-the-middle attack to figure out the contents of each packet and eventually, an MQTT bridge to let Home Assistant control the purifier.
If it sounds like we glossed over a lot, we know — this article is like a master class on reverse engineering. [James] pulled a lot of tools out of his kit for this, and the write-up is clear and concise. You may not have the same mystery fan to work with, but this would be a great place to start reverse engineering just about anything.
Thanks to [ThoriumBR] for the tip.
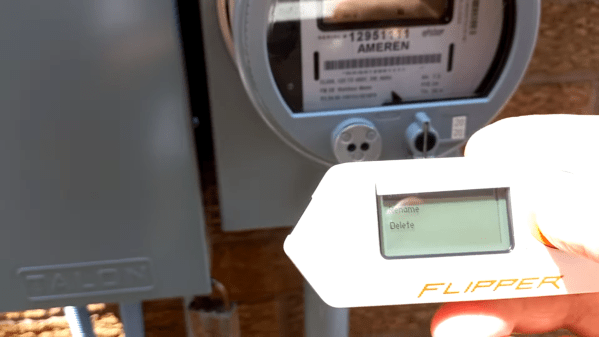
Flipper Zero “Smoking” A Smart Meter Is A Bad Look For Hardware Hackers
Alright, we’re calling it — we need a pejorative equivalent to “script kiddie” to describe someone using a Flipper Zero for annoyingly malign purposes. If you need an example, check out the apparent smart meter snuff video below.
The video was posted by [Peter Fairlie], who we assume is the operator of the Flipper Zero pictured. The hapless target smart meter is repeatedly switched on and off with the Flipper — some smart meters have contactors built in so that service can be disconnected remotely for non-payment or in emergencies — which rapidly starts and stops a nearby AC compressor. Eventually, the meter releases a puff of Magic Smoke, filling its transparent enclosure and obscuring the display. The Flipper’s operator mutters a few expletives at the results, but continues turning the meter on and off even more rapidly before eventually running away from the scene of the crime.
We qualify this as “apparent” because the minute we saw this over on RTL-SDR.com, we reached out to reverse engineer par excellence and smart meter aficionado [Hash] for an opinion. Spoiler alert: [Hash] thinks it’s an elaborate hoax; the debunking starts at the 4:32 mark in the second video below. The most damning evidence is that the model of smart meter shown in the video doesn’t even have a disconnect, so whatever [Peter] is controlling with the Flipper, it ain’t the meter. Also, [Hash] figured out where [Peter] lives — he doxxed himself in a previous video — and not only does the meter shown in the video not belong to the Canadian power company serving the house, StreetView shows that there’s a second meter, suggesting that this meter may have been set up specifically for the lulz.
It should go without saying that Hackaday is about as supportive of hardware experimentation as an organization can be. But there have to be some boundaries, and even if this particular video turns out to be a hoax, it clearly steps over the line. Stuff like this paints a poor picture of what hardware hacking is all about, and leads to unintended consequences that make it harder for all of us to get the tools we need.
Continue reading “Flipper Zero “Smoking” A Smart Meter Is A Bad Look For Hardware Hackers”
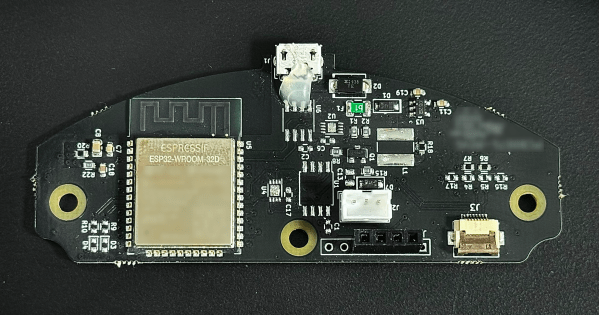
Flipper Zero Mayhem Hat Adds Camera, More Radios
For a device advertised as the “Multi-tool Device for Hackers”, the Flipper Zero already offers a considerable list of onboard capabilities. But some hard decisions had to be made to get the retail price down, so features like WiFi and Bluetooth had to be left off. Luckily, there’s an expansion interface along the top of the device which makes it possible to plug in additional hardware.
One of those expansions is the “Mayhem Hat” from [Erwin Ried]. This board adds many requested features to the Flipper Zero, as well as some that might not seem as obvious. The addition of an ESP32-CAM brings WiFi and Bluetooth to the party, while also unlocking access to the highly-capable ESP32Marauder firmware and the plethora of security research tools therein.
 But the camera also enables some interesting features, such as motion detection and the ability to read QR codes. It even lets you use the Flipper as an impromptu digital camera, complete with an onscreen viewfinder reminiscent of the Game Boy Camera.
But the camera also enables some interesting features, such as motion detection and the ability to read QR codes. It even lets you use the Flipper as an impromptu digital camera, complete with an onscreen viewfinder reminiscent of the Game Boy Camera.
What’s more, the Mayhem Hat features its own expansion capabilities. There’s a spot to plug in either a CC1101 or NRF24l01 radio module, both of which are supported by community developed plugins that allow the user to sniff out and hijack signals. There are also extra pins for connecting your own sensors or hardware. In the demo video below you can see the device automatically detect the popular DHT11 environmental sensor and display the current temperature and humidity readings.
[Erwin] has the Mayhem Hat up for sale on Tindie, but as of this writing, is currently out of stock. Apparently, demand for the add-on boards is just as high as for the Flipper Zero itself — not a huge surprise, given the excitement we saw around this platform during its $4.8 million Kickstarter campaign.
Continue reading “Flipper Zero Mayhem Hat Adds Camera, More Radios”