If you’ve ever sloshed coffee out of your mug and watched the tiny particles scurry to the edges of the puddle, then you’ve witnessed a genuine mystery of fluid mechanics called the coffee ring effect. The same phenomenon happens with spilled wine, and with functional inks like graphene.
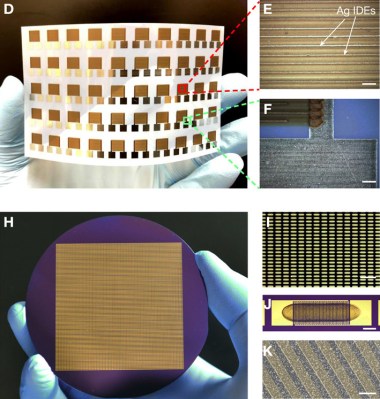
The coffee ring effect makes it difficult to print graphene and similar materials onto silicon wafers, plastics, and other hard surfaces because of this drying problem. There are already a few commercial options that can be used to combat the coffee ring effect, but they’re all polymers and surfactants that negatively affect the electronic properties of graphene.
Recently, a group of researchers discovered that alcohol is the ideal solution. In the case of spilled graphene, the particles fleeing for the edges are naturally spherical. By adding a mixture of isopropyl and 2-butanol alcohol, they get flattened into a pancake shape, resulting in smoother deformation during the drying process and an easier printing process with better results.
Graphene is quite interesting by nature, and has many uses. It can shift from an insulator to a superconductor with the right temperature changes, and it can desalinate sea water for drinking.