Sometimes GPS watches are too good to be left with their stock firmware. [Renaud] opened his Kalenji 300 GPS watch, reverse engineered it in order to upload his own custom firmware.
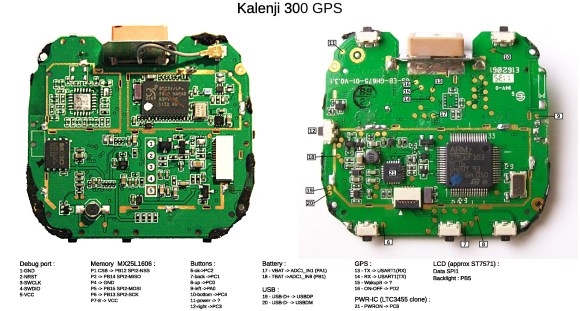
The first step was to sniff the serial traffic between the PC and the microcontroller when upgrading firmware to understand the protocol and commands used. [Renaud] then opened the watch, figured out what the different test points and components were. He used his buspirate with OpenOCD to extract the existing STM32F103 firmware. The firmware helped him find the proper value to store in a dedicated register for the boot loader to start.
By looking at the disassembly code he also found the SPI LCD initialization sequence and discovered that it uses a controller similar to the ST7571. He finally compiled his own program which uses the u8glib graphics library. Follow us after the break for the demonstration video.
Continue reading “Reverse Engineering A GPS Watch To Upload Custom Firmware”