As anyone who is a veteran of many RF projects will tell you, long component leads can be your undoing. Extra stray capacitances, inductances, and couplings can change the properties of your design to the point at which it becomes unfit for purpose, and something of a black art has evolved in the skill of reducing these effects.
RF Biscuit is [Georg Ottinger]’s attempt to simplify some of the challenges facing the RF hacker. It’s a small PCB with a set of footprints that can be used to make a wide range of surface-mount filters, attenuators, dummy loads, and other RF networks with a minimum of stray effects. Provision has been made for a screening can, and the board uses edge-launched SMA connectors. So far he’s demonstrated it with a bandpass filter and a dummy load, but he suggests it should also be suitable for amplifiers using RF gain blocks.
Best of all, the board is open source hardware, and as well as his project blog he’s made the KiCad files available on GitHub for everyone.
It’s a tough challenge, to produce a universal board for multiple projects with very demanding layout requirements such as those you’d find in the RF field. We’re anxious to see whether the results back up the promise, and whether the idea catches on.
This appears to be the first RF network prototyping board we’ve featured here at Hackaday. We’ve featured crystal filters before, and dummy loads though, but nothing that brings them all together. What would you build on your RF Biscuit?


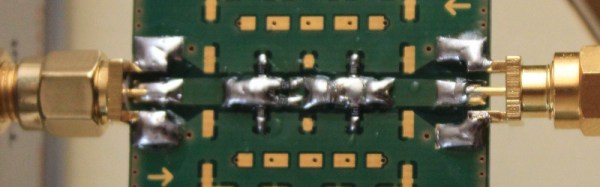




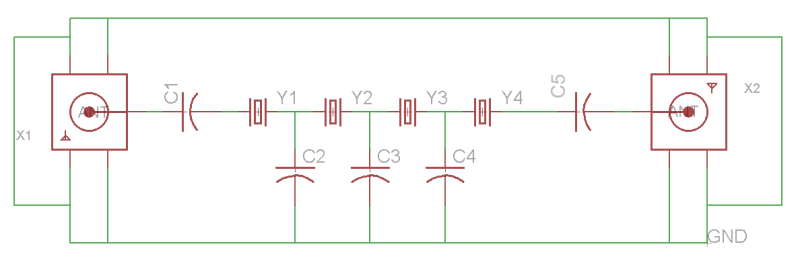
![BPF designed by [Larry]](https://hackaday.com/wp-content/uploads/2016/03/20m_xtalbp_s21close_7-23-2009.gif)