The Amazon Fire TV is Amazon’s answer to all of the other streaming media devices on the market today. Amazon is reportedly selling these devices at cost, making very little off of the hardware sales. Instead, they are relying on the fact that most users will rent or purchase digital content on these boxes, and they can make more money in the long run this way. In fact, the device does not allow users to download content directly from the Google Play store, or even play media via USB disk. This makes it more likely that you will purchase content though Amazon’s own channels.
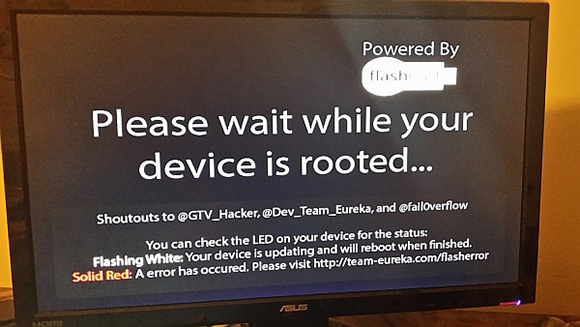
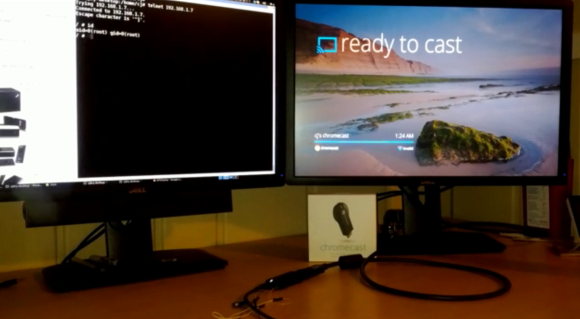
We’re hackers. We like to make things do what they were never intended to do. We like to add functionality. We want to customize, upgrade, and break our devices. It’s fun for us. It’s no surprise that hackers have been jail breaking these devices to see what else they are capable of. A side effect of these hacks is that content can be downloaded directly from Google Play. USB playback can also be enabled. This makes the device more useful to the consumer, but obviously is not in line with Amazon’s business strategy.
Amazon’s response to these hacks was to release a firmware update that will brick the device if it discovers that it has been rooted. It also will not allow a hacker to downgrade the firmware to an older version, since this would of course remove the root detection features.
This probably doesn’t come as a surprise to most of us. We’ve seen this type of thing for years with mobile phones. The iPhone has been locked to the Apple Store since the first generation, but the first iPhone was jailbroken just days after its initial release. Then there was the PlayStation 3 “downgrade” fiasco that resulted in hacks to restore the functionality. It seems that hackers and corporations are forever destined to disagree on who actually owns the hardware and what ownership really means. We’re locked in an epic game of cat and mouse, but usually the hackers seem to triumph in the end.