If you’ve ever purchased a new computer then you are probably familiar with the barrage of bloatware that comes pre-installed. Usually there are system tools, antivirus software trials, and a whole bunch of other things that most of us never wanted in the first place. Well now we can add Superfish spyware to the list.
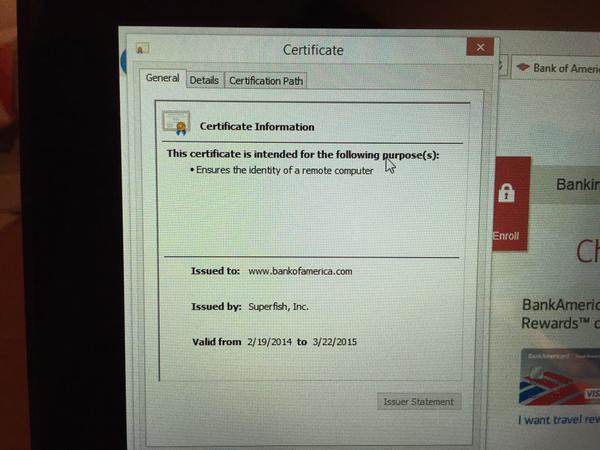
You may wonder what makes this case so special. A lot of PC’s come with software pre-installed that collect usage statistics for the manufacturer. Superfish is a somewhat extreme case of this. The software actually installs a self-signed root HTTPS certificate. Then, the software uses its own certificates for every single HTTPS session the user opens. If you visit your online banking portal for example, you won’t actually get the certificate from your bank. Instead, you’ll receive a certificate signed by Superfish. Your PC will trust it, because it already has the root certificate installed. This is essentially a man in the middle attack performed by software installed by Lenovo. Superfish uses this ability to do things to your encrypted connection including collecting data, and injecting ads.
As if that wasn’t bad enough, their certificate is actually using a deprecated SHA-1 certificate that uses 1024-bit RSA encryption. This level of encryption is weak and susceptible to attack. In fact, it was reported that [Rob Graham], CEO of Errata Security has already cracked the certificate and revealed the private key. With the private key known to the public, an attacker can easily spoof any HTTPS certificate and systems that are infected with Superfish will just trust it. The user will have no idea that they are visiting a fake phishing website.
Since this discovery was made, Lenovo has released a statement saying that Superfish was installed on some systems that shipped between September and December of 2014. They claim that server-side interactions have been disabled since January, which disables Superfish. They have no plans to pre-load Superfish on any new systems.