Judging by the popularity of “How It’s Made” and other shows of the genre, watching stuff being made is a real crowd pleaser. [Jonathan Oxer] from SuperHouse is not immune to the charms of a factory tour, so he went all the way to China to visit the factory where Sonoff IoT devices are made, and his video reveals a lot about the state of electronics manufacturing.
For those interested only in how Sonoff devices are manufactured, skip ahead to about the 7:30 mark. But fair warning — you’ll miss a fascinating discussion of how Shenzhen rose from a sleepy fishing village of 25,000 people to the booming electronics mecca of 25 million that it is today. With growth supercharged by its designation as a Special Economic Zone in the 1980s, Shenzhen is now home to thousands of electronics concerns, including ITEAD, the manufacturers of the Sonoff brand. [Jonathan]’s tour of Shenzhen includes a trip through the famed electronics markets where literally everything needed to build anything can be found.
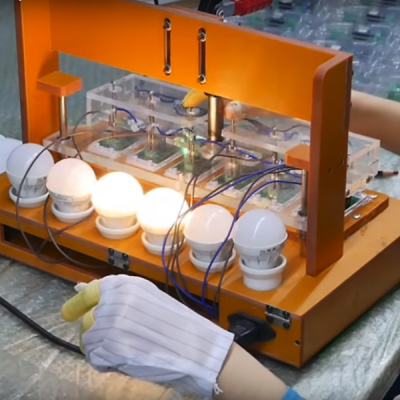
At the ITEAD factory, [Jonathan] walks the Sonoff assembly line showing off an amazingly low-tech process. Aside from the army of pick and places robots and the reflow and wave soldering lines, Sonoff devices are basically handmade by a small army of workers. We lost count of the people working on final assembly, testing, and packaging, but suffice it to say that it’ll be a while before robots displace human workers in electronic assembly, at least in China.
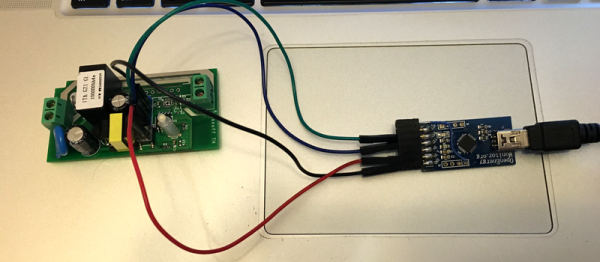
We found [Jonathan]’s video fascinating and well worth watching. If you’re interested in Sonoff’s ESP8266 offerings, check out our coverage of reverse engineering them. Or, if Shenzhen is more your thing, [Akiba]’s whirlwind tour from the 2016 Superconference will get you started.
Continue reading “Sonoff Factory Tour Is A Lesson On Life In Shenzhen”