A few weeks ago, some tantalizing social media posts emerged from a Def Con talk, in which [Sick Codes] broke into the screen control unit for a John Deere tractor live on stage, and proceeded to play a special Deere-themed DOOM level upon it. At the time there was nothing more to go on, but we’re pleased to find out that the whole talk has been put online.
The talk starts with an introduction to the topic, to the basics of the control units within the machine and to the various different ages of Deere screen unit. We find that the earlier machines, which are still at work on farms worldwide, rely on outdated Windows CE versions, though the very latest screens run a Linux variant.
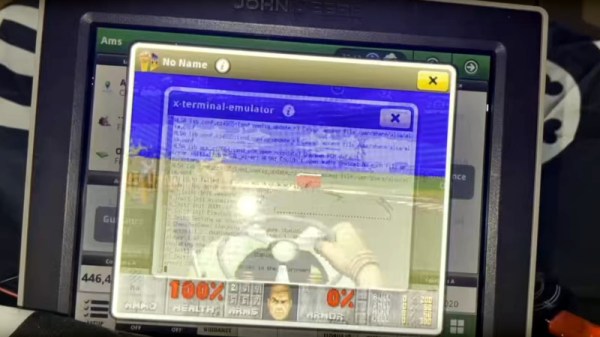
It’s one of these last screens to which he turns his attention, and we’re treated to an in-depth look at some of its secrets. After a lot of dead ends and learning exercises the final result is distilled into a pogo pin adapter for the hardware part, and a simple enough cron job to bypass one of Deere’s defenses by keeping the filesystem writable so a file can be updated. There’s a bit more detail about the special DOOM level too, as a special bonus.
You can see our original mention of this talk, or read some of our past Deere coverage.
Continue reading “Finally We Can Watch The Deere Cracking Def Con Talk”

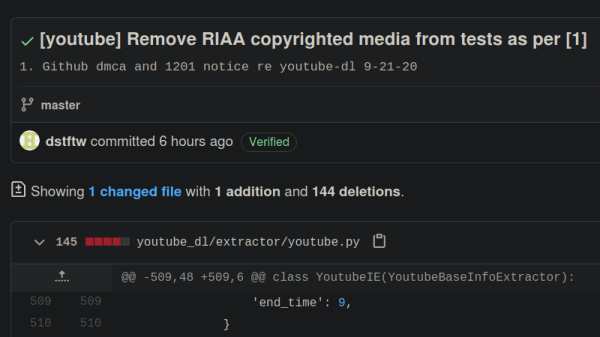
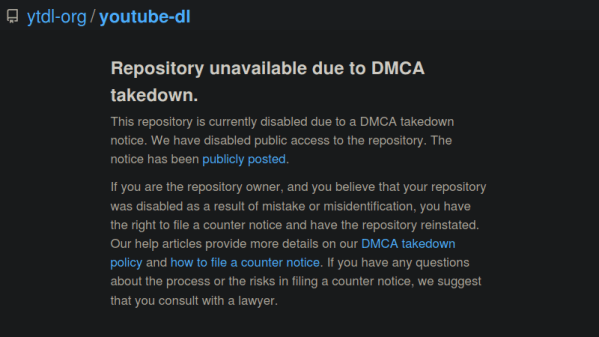
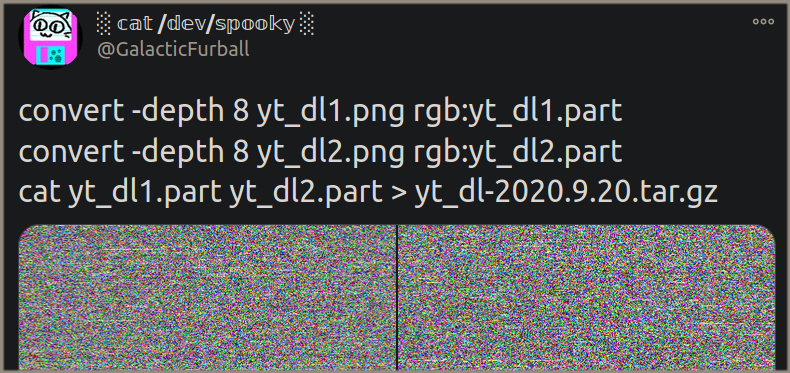

 Both the takedown notice and counter-notice are binding legal documents, sworn under oath of perjury. Notices and counter-notices can be used or abused, and copyright law is famously full of grey zones. The nice thing about GitHub is that they publish all DMCA notices and counter-notices they receive, so
Both the takedown notice and counter-notice are binding legal documents, sworn under oath of perjury. Notices and counter-notices can be used or abused, and copyright law is famously full of grey zones. The nice thing about GitHub is that they publish all DMCA notices and counter-notices they receive, so 













