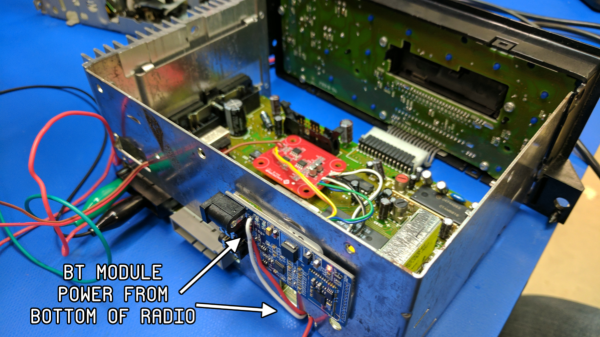
[Charlie Miller] and [Chris Valasek] Have just released all their research including (but not limited to) how they hacked a Jeep Cherokee after the newest firmware updates which were rolled out in response to their Hacking of a Cherokee in 2015.
FCA, the Corp that owns Jeep had to recall 1.5 million Cherokee’s to deal with the 2015 hack, issuing them all a patch. However the patch wasn’t all that great it actually gave [Charlie] and [Chris] even more control of the car than they had in the first place once exploited. The papers they have released are a goldmine for anyone interesting in hacking or even just messing around with cars via the CAN bus. It goes on to chronicle multiple hacks, from changing the speedometer to remotely controlling a car through CAN message injection. And this release isn’t limited to Jeep. The research covers a massive amount of topics on a number of different cars and models so if you want to do play around with your car this is the car hacking bible you have been waiting for.
Jeep are not too happy about the whole situation. The dump includes a lot of background for vehicles by multiple manufactureres. But the 2015 hack was prominent and has step by step instructions. Their statement on the matter is below.
Under no circumstances does FCA condone or believe it’s appropriate to disclose ‘how-to information’ that would potentially encourage, or help enable hackers to gain unauthorized and unlawful access to vehicle systems.
We anticipate seeing an increasing number of security related releases and buzz as summer approaches. It is, after all, Network Security Theatre season.