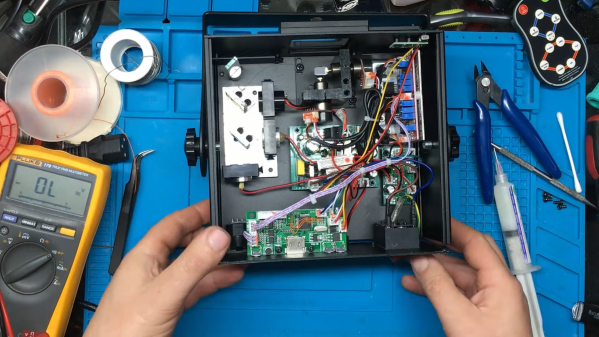
You probably recognize that dreadful feeling when you reboot a gadget after updating its firmware, only to be greeted by a blank screen and an unresponsive device. This apparently happened to the previous owner of a bricked RGB laser projector that [Buy It Fix It] got his hands on: it briefly flashed its laser on power-up but otherwise remained completely dead.
A thorough inspection of the major components didn’t reveal any physical damage, so the issue had to be in software. [Buy It Fix It] managed to connect his Segger J-link programmer to the STM32 main processor and downloaded the contents of its firmware, only to find the remains of a PDF file which seemed to have been accidentally flashed into the chip’s program space. Fixing the device should then just be a matter of restoring the proper firmware, but [Buy It Fix It] wasn’t able to find a copy of it anywhere.
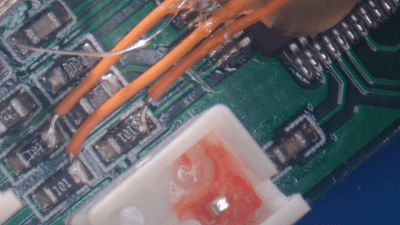 What he did find was Maximus64’s GitHub repository that contained a software mod for a different projector model, as well as its original firmware. Flashing that version didn’t fix [Buy It Fix It]’s projector either, although it did now start to actuate its galvos.
What he did find was Maximus64’s GitHub repository that contained a software mod for a different projector model, as well as its original firmware. Flashing that version didn’t fix [Buy It Fix It]’s projector either, although it did now start to actuate its galvos.
A bit of reverse engineering revealed that the two projectors were very similar from a hardware point of view, but had their laser drivers hooked up to different I/O pins: simply cutting the board traces and soldering some wires to re-route the signals was enough to bring the projector back into a working state.
Having to modify hardware in order to make it fit a piece of software is unfortunate, but sometimes you just have to make do with what you’ve got. If you’ve got no firmware to begin with, then you might even have to write your own from scratch.
Continue reading “Laser Projector Needs Hardware Hack After Software Mod”