Join us on Wednesday, May 13 at noon Pacific for the Pentesting Hack Chat with Eric Escobar!
Ask anyone in this community to name their dream jobs and chances are pretty good that penetration tester will be somewhere on the shortlist. Pentesters are allowed — nay, encouraged — to break into secure systems, to test the limits and find weak points that malicious hackers can use to gain access. The challenge of hacking and the thrill of potentially getting caught combined with no chance of prosecution? And you get paid for it? Sounds good to us!
Professional pentesting is not all cops-and-robbers fun, of course. Pentesters have to stay abreast of the latest vulnerabilities and know what weaknesses are likely to exist at a given facility so they know what to target. There are endless hours of research, often laborious social engineering, and weeks of preparation before actually attempting to penetrate a client site. The attack could be as complex as deploying wireless pentesting assets via FedEx, or as simple as sprinkling thumb drives in the parking lot. But when it comes, a pentest often reveals just how little return companies are getting on their security investment.
As a consultant for a security firm, Eric Escobar gets to challenge companies on a daily basis. He’s also a regular on the con circuit, participating in challenges like Wireless CTF at DEF CON… until he won too many times. Now he helps design and execute the challenges, helping to share his knowledge with other aspiring pentesters. And he’ll stop by the Hack Chat to do the same with us, and tell us all about the business of keeping other businesses in business.
 Our Hack Chats are live community events in the Hackaday.io Hack Chat group messaging. This week we’ll be sitting down on Wednesday, May 13 at 12:00 PM Pacific time. If time zones have got you down, we have a handy time zone converter.
Our Hack Chats are live community events in the Hackaday.io Hack Chat group messaging. This week we’ll be sitting down on Wednesday, May 13 at 12:00 PM Pacific time. If time zones have got you down, we have a handy time zone converter.
Click that speech bubble to the right, and you’ll be taken directly to the Hack Chat group on Hackaday.io. You don’t have to wait until Wednesday; join whenever you want and you can see what the community is talking about. Continue reading “Pentesting Hack Chat This Wednesday”










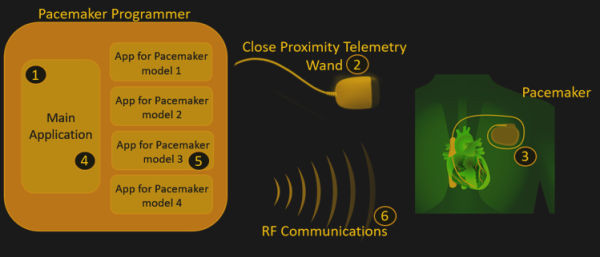
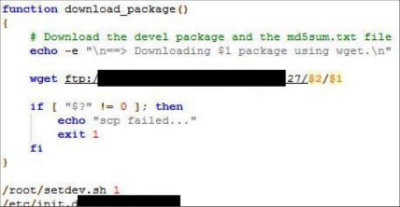 The programmers’ firmware update procedures were also flawed, with hard-coded credentials being very common. This allows an attacker to setup their own authentication server and upload their own firmware to the home monitoring kit. Due to the nature of the hack, the researchers are not disclosing to the public which manufacturers or devices are at fault and have redacted some information until these medical device companies can get their house in order and fix these problems.
The programmers’ firmware update procedures were also flawed, with hard-coded credentials being very common. This allows an attacker to setup their own authentication server and upload their own firmware to the home monitoring kit. Due to the nature of the hack, the researchers are not disclosing to the public which manufacturers or devices are at fault and have redacted some information until these medical device companies can get their house in order and fix these problems.