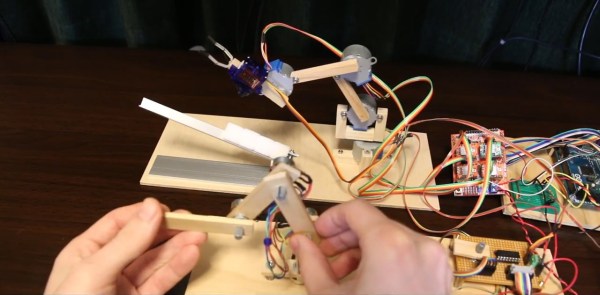
[Tobias Kuhn] had watched a YouTube video about a robot arm which used servo motors, and wanted to try making one himself. But he found it hard to get slow or smooth movements out of the servos. Even removing the microcontroller and trying to work with the servo’s driver-IC and potentiometer from an Arduino Nano didn’t get him satisfaction.
Then he found the very affordable 28BYJ-48 stepper motor. After some experimenting, he came up with a smooth moving robot arm with four steppers controlled from an Arduino Mega and A4988 stepper motor drivers. Rather than write a bunch of stepper motor code himself, he installed and ran a four-axis fork of grbl on the Arduino, turning it into a stepper motor controller. One minor hitch was that the A4988 motor drivers are for bipolar stepper motors but 28BYJ-48 steppers are unipolar. Luckily he knew of a very simple hack which our [Brian Benchoff] wrote about for turning a unipolar motor into a bipolar motor.
To tell the robot arm what to do, he built a replica arm with potentiometers in place of the stepper motors. As he manipulates the replica, the values of the potentiometers are read by a Raspberry Pi and some custom Python code which sends the appropriate G-code to the Arduino/grbl controlled robot arm. There’s a bit of a lag but when he moves the replica arm, the robot arm does the same move. See it in action in the video below.