[Harrison] has been busy finding the sweeter side of quarantine by building a voice-controlled, face-tracking M&M launcher. Not only does this carefully-designed candy launcher have control over the angle, direction, and velocity of its ammunition, it also locates and locks on to targets by itself.
Here comes the science: [Harrison] tricked Alexa into thinking the Raspberry Pi inside the machine is a smart TV named [Chocolate]. He just tells an Echo to increase the volume by however many candy-colored projectiles he wants launched at his face. Simply knowing the secret language isn’t enough, though. Thanks to a little face-based security, you pretty much have to be [Harrison] or his doppelgänger to get any candy.
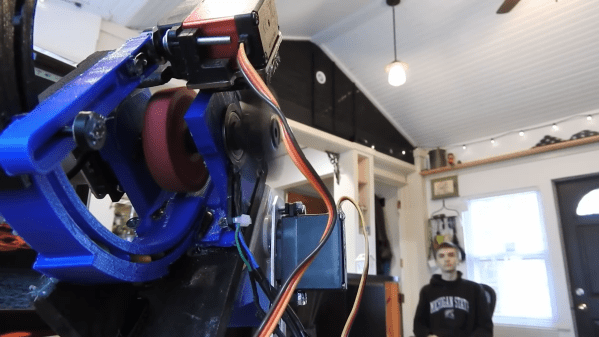
The Pi takes a picture, looks for faces, and rotates the turret base in that direction using three servos driven by Arduino Nanos. Then the Pi does facial landmark detection to find the target’s mouth hole before calculating the perfect parabola and firing. As [Harrison] notes in the excellent build video below, this machine uses a flywheel driven by a DC motor instead of being spring-loaded. M&Ms travel a short distance from the chute and hit a flexible, spinning disc that flings them like a pitching machine.
We would understand if you didn’t want your face involved in a build with Alexa. It’s okay — you can still have a voice-controlled candy cannon.