Git is powerful, but with great power comes the ability to really bork things up. When you find yourself looking at an inscrutable error message after an ill-advised late-night commit, it can be a maximum pucker-factor moment, and keeping a clear enough head to fix the problem can be challenging. A little proactive social engineering may be in order, which is why Jonathan Bisson wrote git-undo, a simple shell script that displays the most common un-borking commands he’s likely to need. There are other ways to prompt yourself through Git emergencies, like Oh Shit, Git (or for the scatologically sensitive, Dangit Git), but git-undo has the advantage of working without an Internet connection.
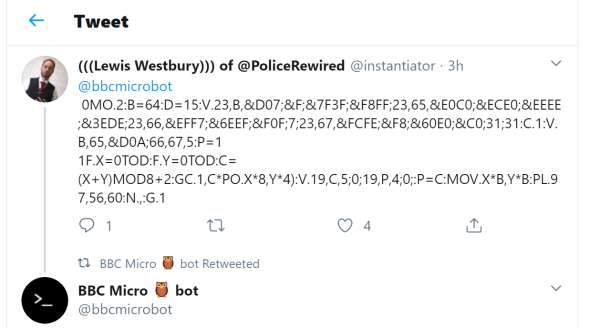
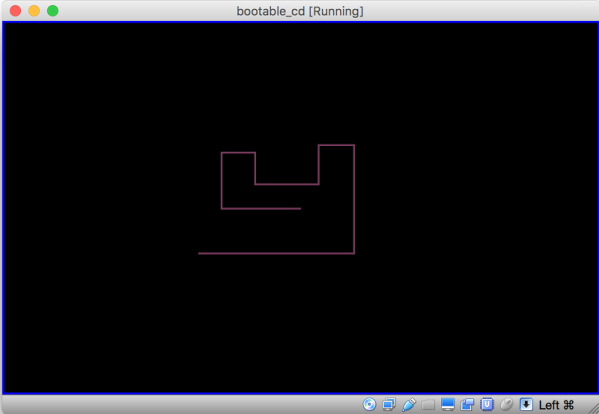
Suddenly find yourself with a bunch of time on your hands and nothing to challenge your skills? Why not try to write a program in a single Tweet? The brainchild of Dominic Pajak, the BBC Micro Bot Twitter account accepts tweets and attempts to run them as BASIC programs on a BBC Microcomputer emulator, replying with the results of the program. It would seem that 280 characters would make it difficult to do anything interesting, but check out some of the results. Most are graphic displays, some animated, and with an unsurprising number of nods to 1980s pop culture. Some are truly impressive, though, like Conway’s Game of Life written by none other than Eben Upton.
The COVID-19 pandemic is causing all sorts of cultural shifts, but we didn’t expect to see much change in the culture of a community that’s been notoriously resistant to change for over a century: amateur radio. One of the most basic facts of life in the amateur radio world is that you need a license to participate, with governments regulating the process. But as a response to the pandemic, Spain has temporarily lifted licensing requirements for amateur radio operators. Normally, an unlicensed person is only allowed to operate on amateur bands under the direct supervision of a licensed amateur. The rules change allows unlicensed operators to use a station without supervision and is intended to give schoolchildren trapped at home an educational experience. In another change, some countries are allowing special callsign suffixes, like “STAYHOME,” to raise awareness during the pandemic. And the boom in interest in amateur radio since the pandemic started is remarkable; unfortunately, finding a way to take your test in a socially distant world is quite a trick. Our friend Josh Nass (KI6NAZ) has some thoughts about testing under these conditions that you might find interesting.
And finally, life goes on during all this societal disruption, and every new life deserves to be celebrated. And when Lauren Devinck made her appearance last month, her proud parents decided to send out unique birth announcement cards with a printed circuit board feature. The board is decorative, not functional, but adds a distinctive look to the card. The process of getting the boards printed was non-trivial; it turns out that free-form script won’t pass most design rule tests, and that panelizing them required making some compromises. We think the finished product is classy, but can’t help but think that a functional board would have really made a statement. Regardless, we welcome Lauren and congratulate her proud parents.