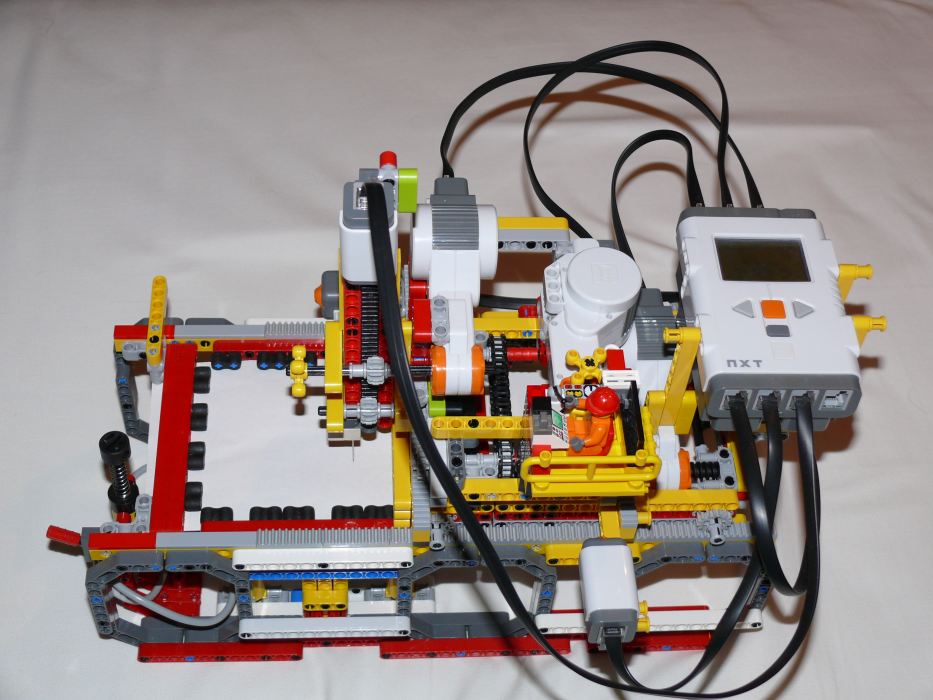
Check out this awesome tool that [Alfonso Martone] built and wrote in to tell us about: a pin plotter made entirely from Lego (except for the addition of a pin in one brick). [Alfonso] has managed to get 33dpi resolution with a “printable” area of 90x70mm. The NXT device reads 1bit bitmapped images in PBM format and outputs onto a sheet of paper, which is held in place by Lego pneumatics pushing against rubber Lego bricks. Output is not what you might call speedy, though: it takes 35-40 minutes to output a drawing with 1,500 holes.
Month: August 2008
IPhone With A Light-up Apple Logo
[youtube=http://www.youtube.com/watch?v=VgfyUsjwGwM&hl=en&fs=1&rel=0&color1=0x3a3a3a&color2=0x999999]
If you feel that your iPhone alone no longer carries the cachet it once did, what with the price dropping and all, this may be just the modification that you need to stand out among the crowd. iPhones.ru has a teaser glimpse of an iPhone hack that causes the Apple logo on the back of the device to light up when the screen is turned on. Details are sketchy, but it appears that the hack involves replacing the metal insert on the back of the phone with an LED-equipped plastic one; custom software allows the user to select the brightness of the glowing effect independently of screen brightness… or maybe they’re just using the backlight.
Biometric Locks Turned Trojan

In the same vein as our recent Defcon article on biometric cloning, White Wolf Security has released this article about turning a biometric door lock into a trojan. They note that there are many common ways to break into one, from harvesting fingerprints to using gummy bears to fake a finger. This hack involves having full access to the unit so you can disassemble it.
The unit has a system built-in where you can touch a 9-volt battery to some connectors on the bottom to power it in case of a building power failure. The researchers simply routed some wires from the motorized lock to the plates used for the 9-volt and then reassembled the lock. The door can then be opened at any time without verification, even if the software on the unit is reset.
[Thanks, dwight]
Robot That Runs On Rat Brain Cells
Scientists at the University of Reading have created a robot that runs not on microprocessors, but on brain cells extracted from a rat fetus. The robot is equipped with several sensors which stimulate the rat neurons whenever the robot approaches a wall; the response of the neurons then determines whether the robot avoids the wall or crashes into it. The truly fascinating bit is that the rat brain cells don’t automatically know how to respond to the stimuli from the sensors, but instead learn to respond appropriately through repeated stimuli.
No word yet on whether the scientists will teach the robot to sing “Despite all my rage / I am still just a brain in a vat”.
Make A Stretchy Fabric USB Cable
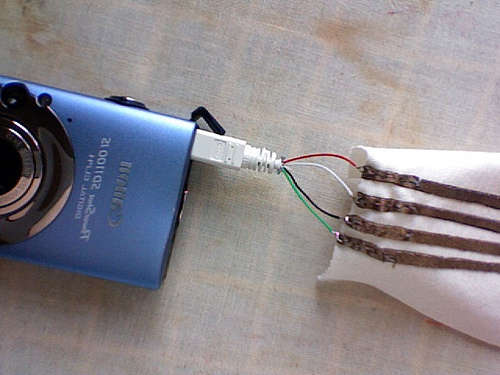
If you’ve been puzzled over a discreet, durable way to sew wiring into your clothing, then puzzle no more: [Plusea] has put together a writeup detailing how to make a USB cable partly out of stretchy cotton fabric. Although the design as detailed doesn’t give much practical use for the invention, we can think of several very effective ways of exploiting this toy. Imagine, for example, placing a USB battery pack into one pocket of a jacket, a portable digital audio recorder in the other, and a lavalier microphone in the lining, thus enabling dozens of hours of covert audio surveillance.
Defcon 16: Biometric Cloning

One of the more novel talks we saw at Defcon was [Zac Franken] presenting on access control systems. He covered several different types, but the real fun was his live demo of bypassing a hand geometry scanners like the one pictured above. With the help of two assistants, 4 pounds of chromatic dental alginate, and 5 liters of water, he made a mold of his hand. The box he placed his hand in had markings to show where the pegs on the scanner are located. After 2 minutes he could remove his hand from the cavity. They then filled the mold with vinylpolysiloxane, making sure to remove all bubbles. 20 minutes later the hand was solid and passed the scanner’s test. This may not be a completely practical attack, but it does defeat the overall idea of biometrics; biometrics are built on the assumption that every person is unique and can’t have their features reproduced.
[Zac] also showed an interesting magnetic card spoofer that emulated all three tracks using coils of magnet wire. We hope to see more about that in the future.
[photo: morgan.davis]
RIAA Pays Out $108,000 To P2P Lawsuit Defendant

[Tanya Andersen], the defendant in Atlantic v. Andersen, has finally been paid $107,951 for reimbursement of legal fees. RIAA lawyers had appealed to get the amount reduced and originally offered $30,000 then $60,000, but [Andersen]’s lawyers convinced the judge to uphold the six-figure sum.
This is a significant setback for industry lawyers who often use illegal discovery techniques and have been criticized for using overly-litigious legal strategies to force defendants to settle. Sadly though, the payout only covers [Andersen]’s legal fees and doesn’t offer any compensation for damages, but a counter-suit filed in Portland, Oregon seeks exactly that. Here’s hoping her lawyers [Lory Lybeck] and [Ben Justus] continue to set favorable legal precedents for defendants of these lawsuits.
As far as the technical side of the discovery methods go, there are many ways to keep the RIAA off your back. The simplest is to disable your P2P client’s available file listing or turning off outbound traffic altogether. Other ways are to use encryption (although this is usually to get around ISP blocks) or download to an offsite machine. Hopefully, though, this judgment and eventual payout will make the recording companies reconsider the amount of lawsuits they file and to use less aggressive legal tactics.










