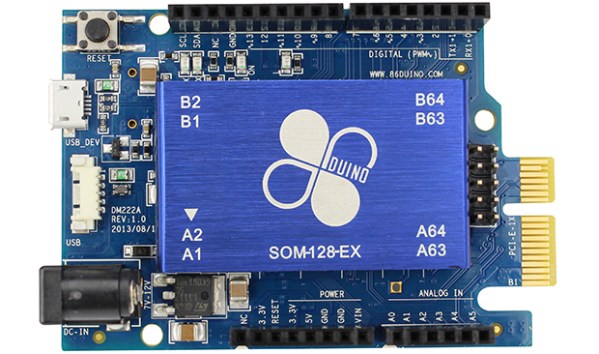
Every week the Hackaday tip line receives an email about a new dev board. The current trend is towards ARM devices, and only once have we seen an x86-based device. Today that count went up to two. It’s called the 86Duino and stuffs an old Pentium II-class machine capable of running DOS, Windows, and Linux into the space of an Arduino,
The 86Duino Zero features, of course, an x86 Vortex86EX processor running at 300 MHz. This board also features 128 MB of RAM, 8MB of Flash and the usual compliment of Arduino pins in a Leonardo-compatible layout. Also on the SoC is a PCIE bus, Ethernet, a USB 2.0 host, and an SD card. There’s a lot of stuff on this board for such a small size.
Compared to the gigahertz-fast ARM boards around, the 86Duino isn’t really that fast, but that’s not the point. There’s obviously a market for extremely tiny x86 boards out there as evidenced by the Intel Galileo, and this board is $30 cheaper than the Intel offering.
There’s no video out on this board, so someone will have to figure out how to attach a graphics card to the PCIE connector before we build a miniaturized old school DOS gaming rig. Still it’s a very neat piece of hardware. If you need to have it now, here’s a vendor.
Thanks [sohaib] for sending this one in.