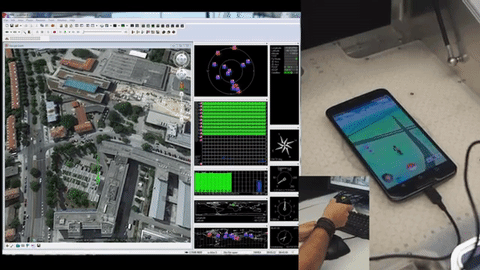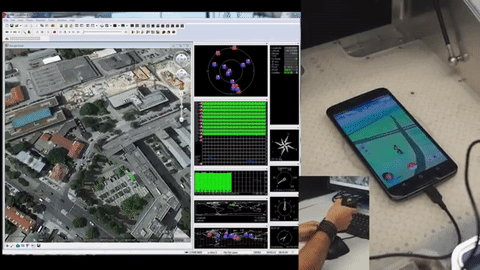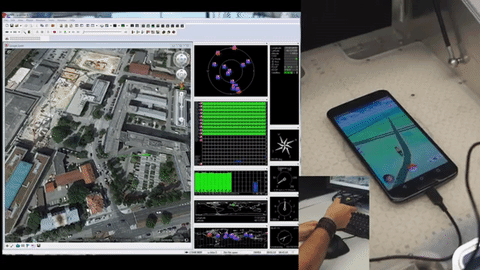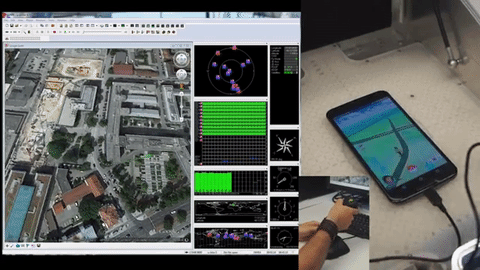
Since Pokemon Go blew up the world a couple of weeks ago we’ve been trying to catch ’em all. Not the Pokemon; we’ve been trying to collect all the hardware hacks, and in particular the most complete GPS spoofing hack. We are now ready to declare the first Grandmaster GPS spoofing hack for Pokemon Go. It broadcasts fake GPS signals to your phone allowing the player to “walk around” the real world using a gaming joystick.
Just about everything about this looks right to us. They’re transmitting radio signals and are doing the responsible thing by using an RF shield box that includes a GPS antenna. Hardware setup means popping the phone inside and hooking up the signal generator and GPS evaluation hardware. Google Earth then becomes the navigation interface — a joystick allows for live player movements, coordinates are converted to GPS signals which are transmitted inside of the box.
Now, we did say “just about right”. First off, that RF shielding box isn’t going to stop your fake GPS signals when you leave the lid open (done so they can get at the phone’s touchscreen). That can probably be forgiven for the prototype version, but it’s that accelerometer data that is a bigger question mark.
When we looked at the previous SDR-based RF spoofing and the Xcode GPS cheats for Pokemon Go there were a number of people leaving comments that Niantic, the devs responsible for Pokemon Go, will eventually realize you’re cheating because accelerometer data doesn’t match up to the amount of GPS movement going on. What do you think? Is this app sophisticated enough to pick up on this type of RF hacking?
Continue reading “We Declare The Grandmaster Of Pokemon Go GPS Cheats”