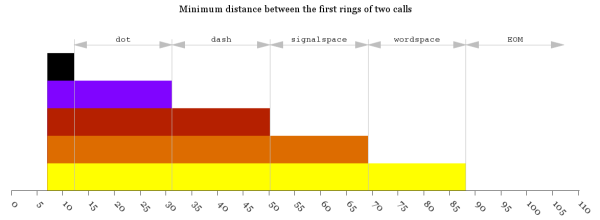
After years of ignoring the emails it’s finally time to get into a conversation with that Nigerian prince you keep hearing from. Robbie Gallagher — an Application Security Engineer with Atlassian in Austin, TX — wanted to find out where perpetrators of phishing emails actually live. Of course you can’t count on the headers of the emails they send you. A better way to track them down is to actually draw them into a conversations, and this means making yourself a juicy target.
Robbie gave an excellent talk on his project Honey-Phish at this year’s Shmoocon. Part of what made it stand out is his narrative on each step of exploring the social engineering technique. For instance, there is already a vibrant community that specializes in forming relationships with scammers. Those who frequent 419 Eater have literally made it into a sport called Scambaiting. The ultimate goal is to prove you’ve baited a scammer is to get the person to take a picture of themselves balancing something on their head. Now the image a the top of this post makes sense, right?
Writing personal emails to your scammer is a great system if you have a lot of time and only want to track down one scammer at a time. Robbie wants to catalog geographic locations for as many as possible and this means automation. Amusingly, the solution is to Phish for Phishers. By automating responses to phishing emails, and enticing the people originating those phishing scams to click on a link, you can ascertain their physical location.




 There are three things that [Gord] has going for him. First off, the Champion Blower and Forge Co. built them to last. Second, he’s not really working on a deadline; the museum doesn’t need it back until May. And third, [Gord] has the tools he needs to do this right.
There are three things that [Gord] has going for him. First off, the Champion Blower and Forge Co. built them to last. Second, he’s not really working on a deadline; the museum doesn’t need it back until May. And third, [Gord] has the tools he needs to do this right.